4 Zero Trust Use Cases for CISOs and IT Managers


Zero trust security provides CISOs, CIOs and IT managers with solutions to a variety of business and architectural needs. Covid-19, for example, has generated a large-scale requirement for secure remote work. In other cases, some departments might work with multiple third parties and ask for a remote access services solution for them. This blog post will cover four common zero trust use cases: privileged access management (PAM), third party access, operational technology (OT) and remote work (WFH). We will show you how to ensure secure zero trust connectivity in each.
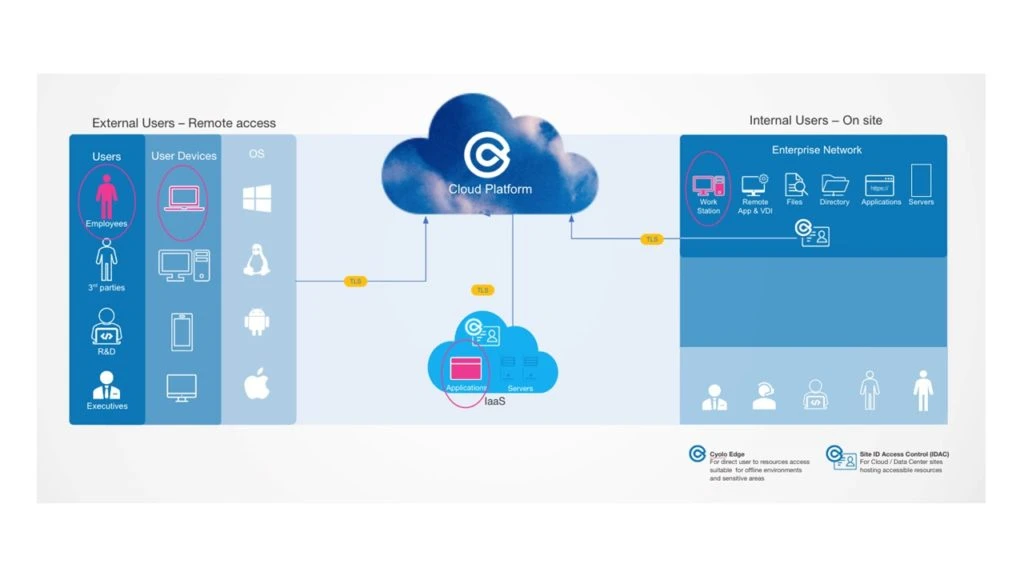
First, let’s see what a comprehensive zero trust architecture looks like:
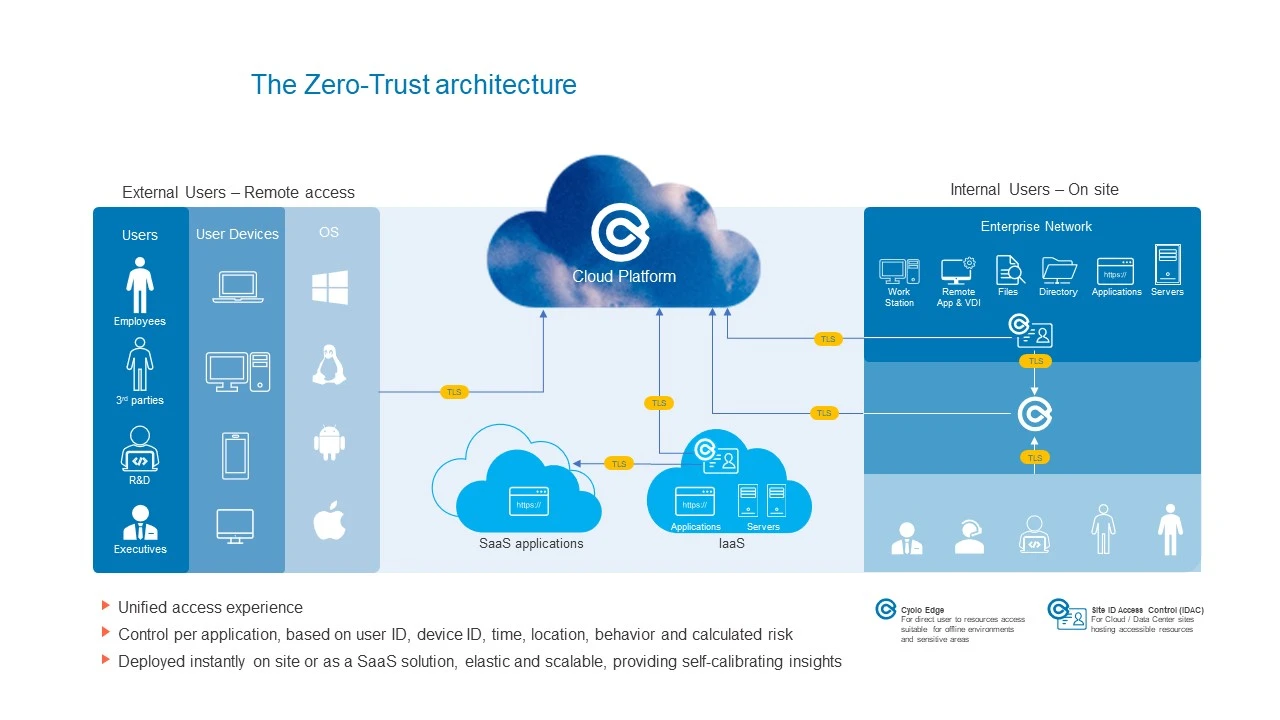
As you can see, this enterprise network diagram consists of multiple types of external users and their devices (managed or unmanaged), applications running from SaaS platforms, applications and resources running from public and private Clouds, Data Centers or co-location sites.
While the diagram shows a standard network, the architecture itself presents a true zero-trust deployment. No inbound network traffic is allowed, so all the published applications and resources are hidden from the eyes of attackers when they are performing reconnaissance and trying to find their way in. All the customer data and secrets are kept in the component that resides in the organizational secure environment and are not accessible even to the zero trust provider. This includes the policies and password vault that are also signed by the customers keys (certificates) and are not visible to anyone.
We recommend having an additional (edge) component that will enable zero trust access from within the network, for eliminating the risk of an internal attacker. Such a component can be used to secure access to critical assets and environments, and even for networks that are not connected to the internet. This ability to secure multiple and even traditional protocols and apps is very important for many organizations.
As you can see, the entire process abides to the zero trust model and this model is safer. No customer data is kept in the cloud, nor is it visible outside of the organizational secure environment. This includes encryption keys, access policies, user directories, etc.
This implementation provides maximum coverage of secure access needs. It supports any application and protocol (including legacy applications), providing secure access from within the network as well as remote access. It also includes multi-factor authentication, single-sign-on, privileged access management capabilities, session recording, risk-based access and direct integration with any identity infrastructure.
Now let’s see how this architecture and these practices can be adapted to different users with different needs. We’ll look at four use cases: Privileged Access Management (PAM), third party access, OT and remote work.
Privileged Access Management (PAM) users require unique access rights. Unfortunately, many times their access isn’t supervised or controlled at all. PAM is about providing specific and controlled access to specific devices, ensuring no server passwords are unknown and enforcing extra security measures like biometric authentication, recording for supervision and full auditing.
Let’s look at an example of a SYS admin originating from within the private network. This user needs to access a few servers.
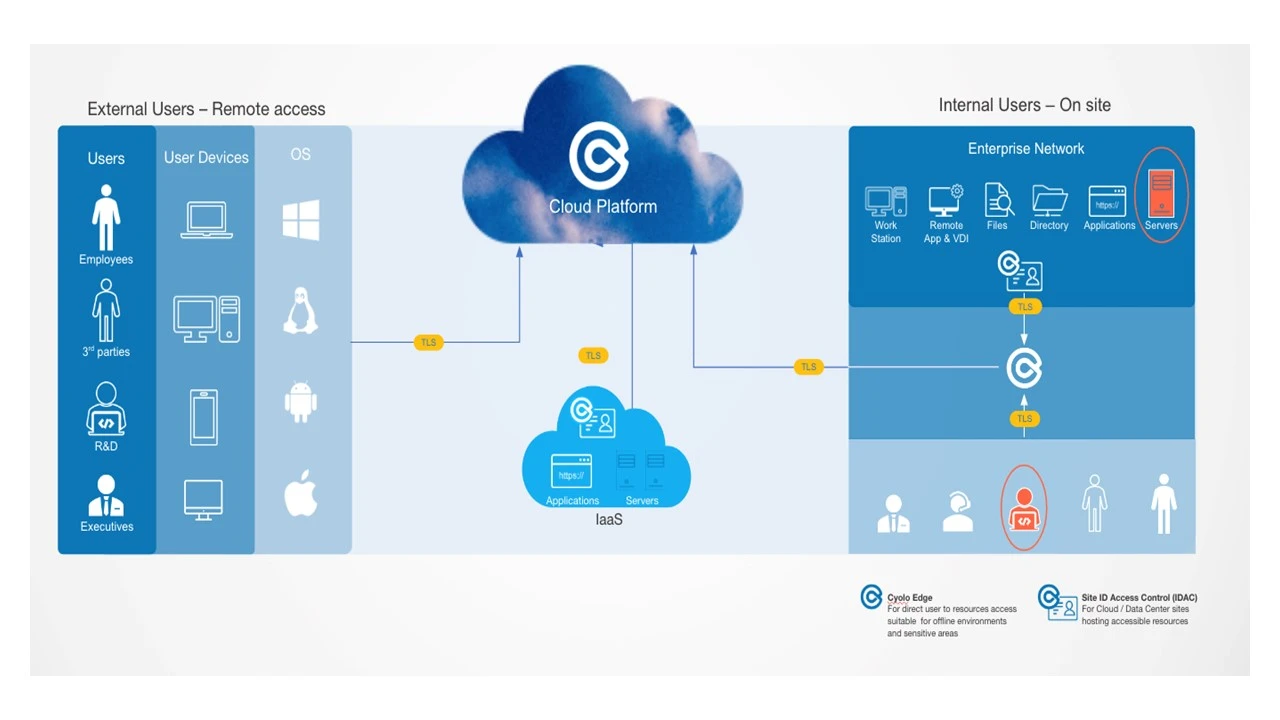
To ensure a secure zero trust journey, it it important to ensure:
Limited access
Access policy enforcement
Logging all actions
Auditing possibilities
For highly sensitive assets, it is also recommended to:
Grant and control the access in real time
Have real time visibility into the admin’s actions during the session
A common use case is connecting suppliers, partners and other third party users. These entities are part of the ecosystem, and connectivity is required for business collaboration. The CISO, IT Manager or Network Manager needs to ensure secure and controlled external access of users with unmanaged devices who are accessing organizational information assets.
Let’s look at an example of a supplier who needs to access the organization ERP and one of the servers.
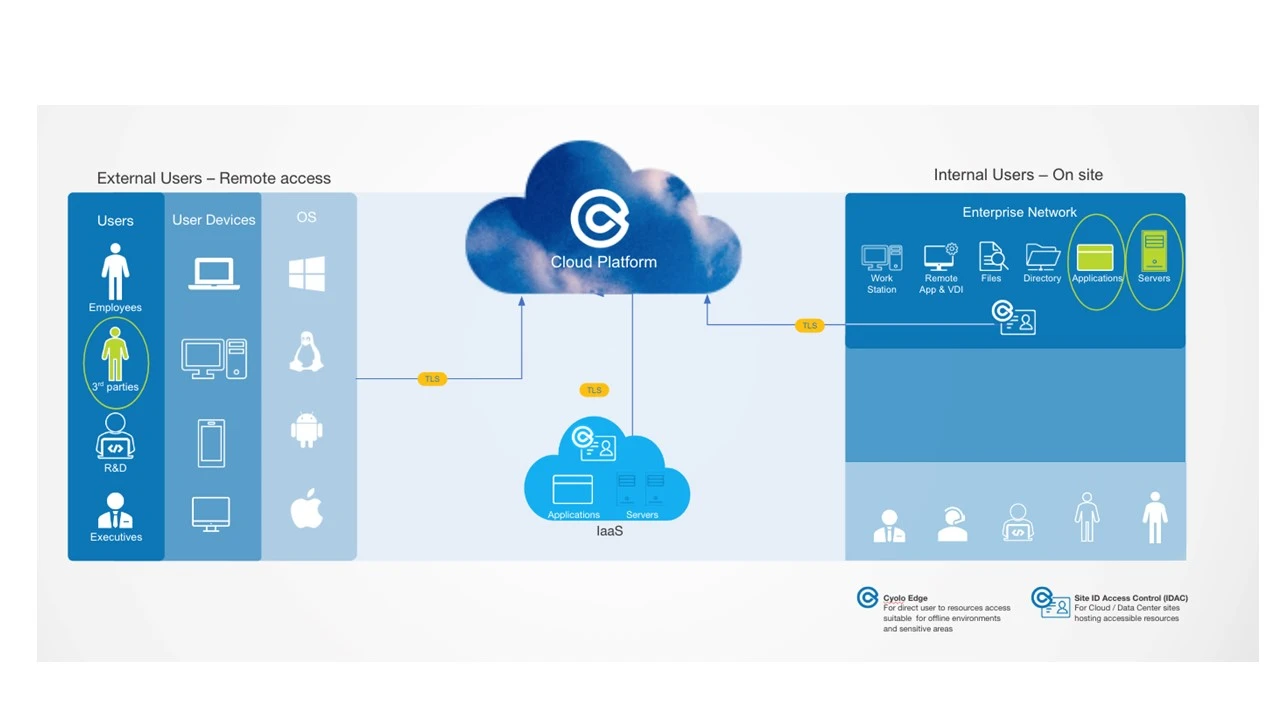
In this case, it is recommended to:
Require explicit real-time approval
Grant real time limited access
Ensure specific, limited rights. For example, limit copy/paste or file transfer rights in order to reduce risk of data leaks and malware outbreaks.
These security measures reduce the need to connect the supplier through a VPN or to provide suppliers with your organization’s managed devices. CISOs and CIOs can thus facilitate business collaboration in a secure and easy way.
Operational technologies require secure access for specific clients. All while limiting network access and keeping production lines running.
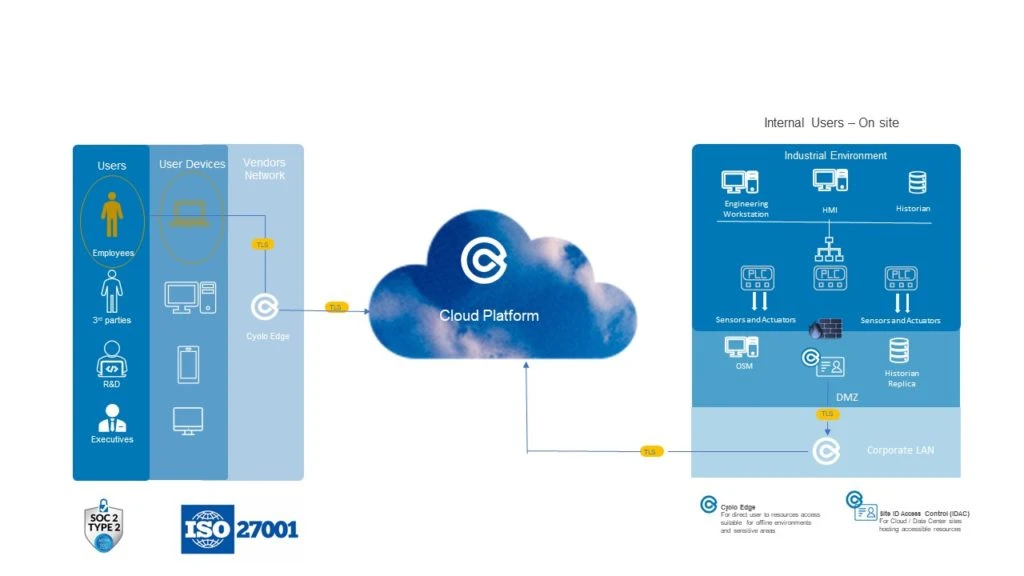
To ensure production lines operate at all times, we recommend:
Network access through an ICS subnet
Biometric authentication, instead of passwords
Recording of activities in the network, for supervision
Monitoring access control in one place in the network, both for online and offline environments
This has become a popular use case lately. Businesses need to securely connect remote employees, using managed or unmanaged devices, to the organization’s applications, servers, desktops and files. This is important for ensuring business continuity.
Let’s look at an example of an employee WFH using his/her personal laptop, who needs to access the organization CRM and the office desktop.
To provide a smooth and secure connection, it is recommended to:
Verify the ID before access
Encrypt the traffic
Enforce MFA
Monitor activities in real time to detect suspicious behavior
Require explicit real-time approval from someone trusted within the organization, in real time
That’s it! We hope you can now implement zero trust for privileged access management, third parties, OT environments, and remote work scenarios.

