CMMC and SOC 2: An Intro to Security Compliance and Why It Matters

Written By
Dedi Yarkoni

Security regulations help companies build and maintain their information security strategy. Compliance to these regulations sends a message of trust between the company and its customers: it shows that the company is taking advanced measures to protect and preserve data privacy. It is also required for partnering with certain organizations, like the DoD. This is especially important given the growing number of data breaches and cyber crimes, which result in an estimated loss of $600 billion annually in the US alone. Not to mention the personal grievances for users.
This blog post will explain two important information regulations: CMMC and SOC 2, and when you should use each one.
To combat the threats of cybercrime on US economic and national security, the Department of Defense (DoD) is introducing CMMC - Cybersecurity Maturity Model Certification. Let’s see what this model means.
CMMC is a security standard model developed by the U.S Department of Defense. The goal of the model is to enhance the security posture of the Defense Industrial Base and reduce cyber security threats. This will be done by better protecting information and assets that are considered CUI (controlled unclassified information), i.e sensitive but not classified. CMMC comprises more stringent regulations for protecting CUI. Future DoD acquisitions will have to comply with CMMC.
The underlying idea behind the CMMC is that security is foundational and should not be traded. Cost, schedule and performance are based on cybersecurity, instead of security being another tradable element of a project, service or product.
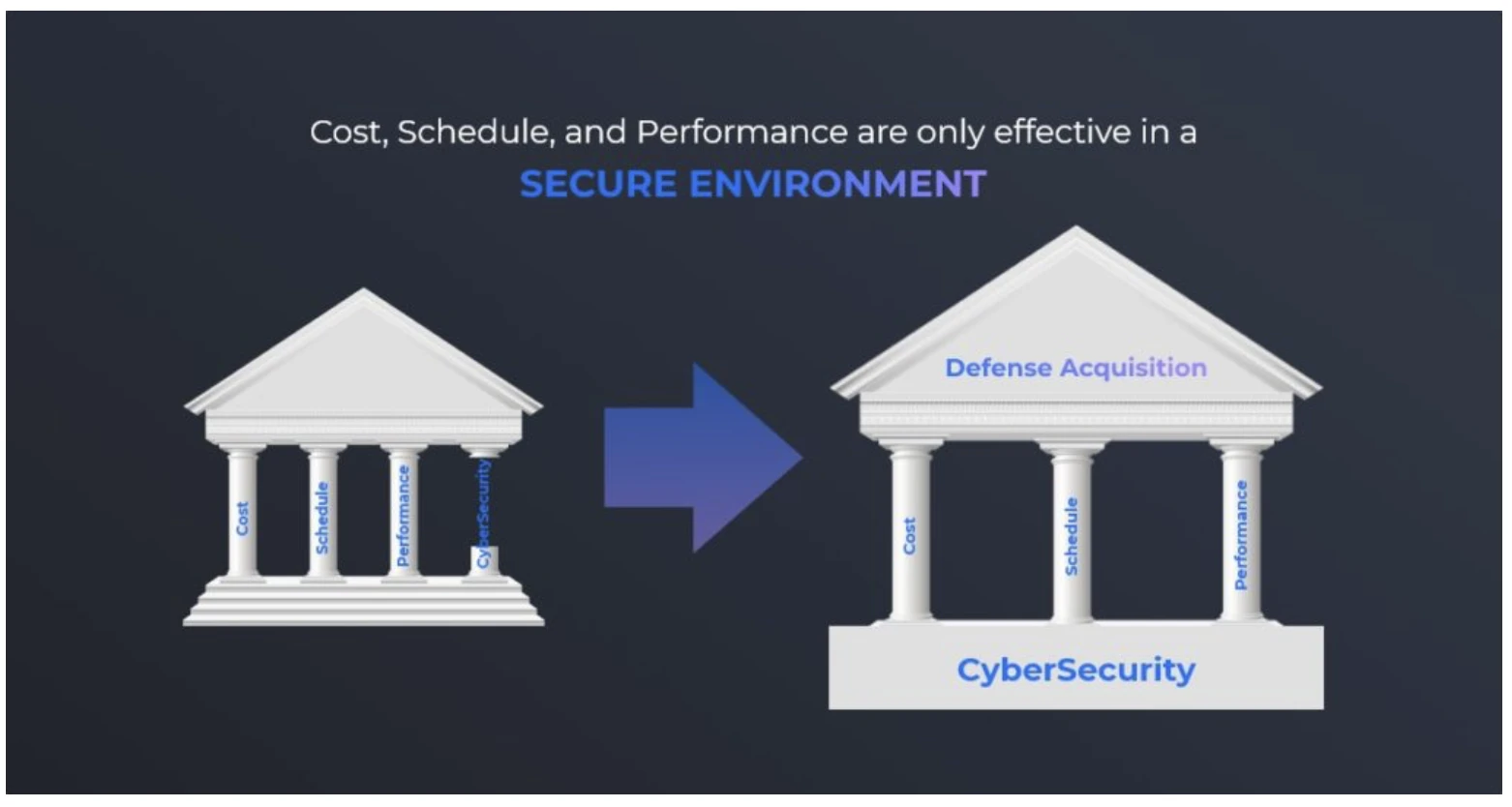
CMMC is divided into 17 security domains like “Access Control” and “Identification and Authentication”. Each domain is divided into five maturity levels. Contractors and businesses can get certified in any level, according to the requirements of the DoD for each level (see section below for more details). Contracts will detail which level is required to be compliant with them.
Compliance with CMCC is intended to be cost-effective and affordable for small businesses at lower levels. Third parties will conduct the audits to verify compliance. A CMMC certification is valid for three years.
300,000 business, organizations and universities are a part of the DoD supply chain, and are involved in military weapons systems, for research, development, acquisition, production and operation. These contracts are vulnerable to cyber attacks by U.S government adversaries, aimed at gaining intellectual and controller information. The rate of attacks is increasing, putting the DoD and national security at risk.
The dollar value of the risk is priced at $600 billion per year, and is expected to exceed $5 trillion by 2024. In addition, information leaks have implications on national morale, citizen trust and even lives.
The CMMC model was developed by the DoD with research and development centers, to facilitate in implementing cybersecurity measures among contractors while improving security posture and reducing risk.
The first version of CMMC was released to the public in January 2020.
Some companies will be required to meet CMMC by the end of September 2020.
All new DoD contracts will contain CMMC requirements by 2026.
CMMC comprises 17 domains of technical capabilities. These are:
Access Control (AC)
Asset Management (AM)
Awareness and Training (AT)
Audit and Accountability (AU)
Configuration Management (CM)
Identification and Authentication (IA)
Incident Response (IR)
Maintenance (MA)
Media Protection (MP)
Personnel Security (PS)
Physical Protection (PE)
Recovery (RE)
Risk Management (RM)
Security Assessment (CA)
Situational Awareness (SA)
Systems and Communications Protection (SC)
System and Information Integrity (SI)
Each of these domains has five certification levels of processes and five certification levels of practices.
The five levels of processes are the same across all domains. They include:
Level 1: No processes required
Level 2: Establish policies for all practices + document practices.
Level 3: Establish, maintain and resource a plan for activities + Level 2.
Level 4: Review and measure activities for effectiveness + Level 3.
Level 5: Standardize and optimize a documented approach for the entire organization + Level 4.
The five levels of practices vary from domain to domain. They were decided on and structured according to existing regulations like FAR and NIST, together with additional requirements created by the DoD. You can find the list of requirements per domain here.
If you wish to work with the DoD, the answer is yes. CMMC will be required for any company or contractor in their supply chain, to different extents, based on the contract. It is also our belief that this model will be adopted by additional governmental agencies and by private companies, as a baseline security and compliance model, in the future. This is similar to how GDPR is often enacted as privacy guidelines for companies, even if they are not required to comply.
Cyolo’s simple zero trust access solution is compliant for three of the CMMC’s domains:
Access Control (AC)
Audit and Accountability (AU)
Identification and Authentication (IA)
There are still many unknowns about CMMC. SOC 2, on the other hand, has been around for a while. Here’s what you need to know.
SOC 2 is an audit report detailing the information security policies and procedures followed by the audited company. In other words, it shows how these companies are managing their customer data. Developed by AICPA - the American Institute of Certified Public Accountants, SOC2 should be looked into by any company or service that stores customer data in the cloud.
SOC 2 is sometimes confused with ISO-27001. ISO-27001 is a top-down approach for managing information security systems. It is focused on management and processes. SOC 2 on the other hand, is focused on the “how”, i.e how the policies are being implemented.
There are two types of SOC 2 reports:
Type 1 – An opinion by the service auditor. This report is based on the description of the organizational systems provided by company management to the auditing accounting firm
Type 2 - An opinion by the service auditor + a description of the systems tests and results operated by the auditor.
SOC 2 is based on five principles, dubbed the 'Trust Service Principles.'
They are:
Security - Protecting information and systems from unauthorized access, information disclosure, and system damage, which could compromise their security and privacy. Requires activities like firewalls, multi-factor authentication (MFA) and intrusion detection. This is the only mandatory principle of SOC 2.
Availability - Ensuring information and systems are available for operation and use. Requires activities like performance monitoring, disaster recovery and incident handling.
Processing Integrity - Ensuring system processing is complete, accurate and valid. Requires activities like QA and process monitoring.
Confidentiality - Protecting confidential information from being accessed in an unauthorized manner and the ability to remove it from the systems. Requires activities like encryption, access controls and firewalls.
Privacy - Security of personal information. Requires activities like access control, MFA and encryption.
SOC 2 compliance is provided by an external auditor who is a CPA or an accountancy firm. The auditor reviews that the controls are operating effectively to meet the objectives of the trust principles.
Before the audit, management should prepare:
A description of the service organization’s system
A written assertion testing to the description’s fairness and that the system’s design meets the trust criteria. Type 2 also asks how the controls operate effectively
Representations to the accounting firm
Then the auditor provides a report based on the description (type 1) or also tests for determining the effectiveness of the controls in place (type 2).
SOC 2 reports take a few weeks to prepare and they are required annually.
If you have customer data in the cloud, then yes. SOC 2 is especially recommended for companies in the following industries: fintech, cloud service, healthcare, data centers, sales automation and intellectual property. SOC 2 not only promotes your brand as a trustworthy one, it also helps create a secure-centric company culture, and enhances your security and data management capabilities.
Cyolo’s simple zero trust solution is compliant for multiple SOC 2 trust principles.
We can help you with access control, accountability, managing privileged users, and more.
Contact us to discuss how we can help you achieve SOC 2 level 2 compliance.
With so many solutions out there, coupled with so many data breaches and privacy violations, it’s hard for consumers to trust products. Regulations and compliance models like CMMC, SOC 2, ISO-27001 and more send assurance to users and companies that their data is secure and that measures are in place to maintain their privacy and protect their assets.
Compliance also ensures companies invest resources and efforts into protecting users and their crown jewels. It puts them in a state of mind that is security-focused, as they are reminded not to take the issue lightly.
Finally, security reaps financial benefits. By preventing data breaches, brute force attacks, malware, and identity theft, security solutions not only block cybercriminals but also enable growth and business success.
Cyolo’s zero trust solution can help you protect your users, data and systems. By implementing zero trust, Cyolo ensures secure access inside and outside the network for employees, third parties and partners.

Author
Dedi Yarkoni is CTO and co-founder of Cyolo. Prior to Cyolo, Dedi worked as the Cyber Lab Research Team Leader at GE Digital and the Applicational Security Technical Program Manager at AWS. He is also a certified ethical hacker and a veteran of the Israeli Navy.

