

As most of us were either logging off or winding down our days on November 1, 2022, one of the most popular file-sharing services, Dropbox, began to report on a security incident. The breach, which occurred an entire month earlier on October 14, started when GitHub notified Dropbox of suspicious activity.
The investigation has shown that the attacker(s) found code that contained credentials and API keys used by Dropbox engineers. In addition, several thousand records of Dropbox employees, customers, and vendors were also found in this code.
How did this happen?
In 2022 we have seen numerous breaches across the biggest names in tech, including Okta, Cisco, Uber, and now Dropbox. These companies have undoubtedly invested millions of dollars into ensuring they are as secure as possible – so how do breaches keep happening to the companies that either sell products to secure customers, or are responsible for safeguarding sensitive information?
The riskiest attack surface vector to secure is always the workforce. This isn’t to imply that users are incompetent – just that we are human and we all inevitably make mistakes. The catalyst of the Dropbox breach was a phishing email that impersonated a platform used by Dropbox developers called CircleCI – for continuous integration and delivery (in other words, their software supply chain). This email asked for users to log in with their GitHub account to accept a new privacy policy.
As is so often the case, the phishing message looked legitimate. At a quick glance, it is readily apparent why a user might click on this bad message. Honestly, how deeply do any of us read the dozens if not hundreds of emails that arrive in our inboxes every day?
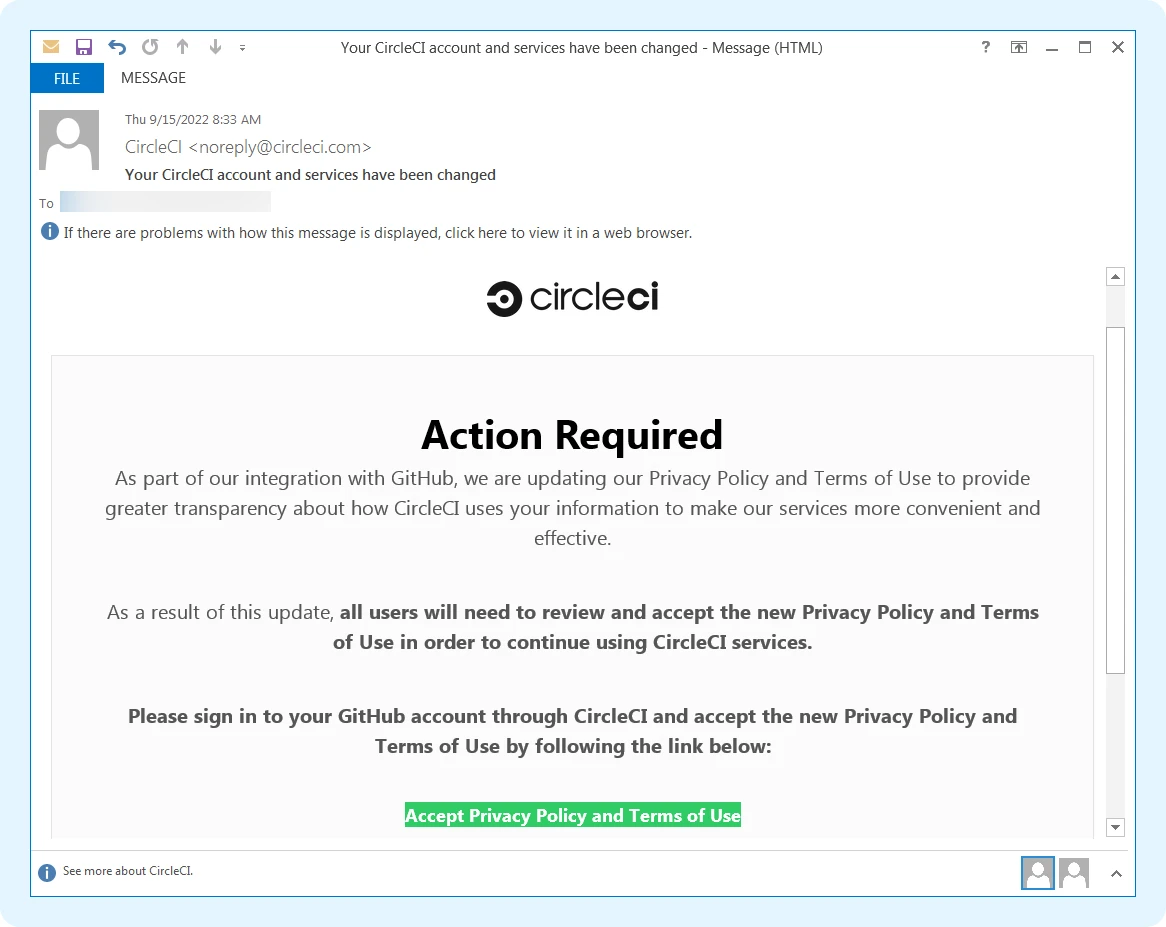
(Photo Credit: BleepingComputer)
The phishing email was purposefully crafted to allow the attacker to grab GitHub credentials, as most source code and ongoing projects are worked on and stored within the GitHub platform. The attacker then used those credentials to access GitHub, acting like a normal user – and ultimately collecting over 100 repos of code from GitHub.
Interestingly enough, GitHub reported that content exfiltration was taking place through some type of anonymizer service, such as a Virtual Private Network (VPN) or proxy, almost immediately after the attack took place. In September 2022, GitHub also reported that many customers were getting phishing emails also “from” CircleCI.
The key here is that systems and processes were in place to detect symptoms of a breach and allowed GitHub to jump right on their investigation and notify all of those effected.
Relying on security systems that primarily protect the network perimeterhas become problematic since the widespread move to remote work. After all, can you really secure the traditional perimeter when your people are now outside the physical boundaries of the office? Security incidents like what happened with Dropbox continue to demonstrate that the network perimeter is obsolete and identity is our new perimeter.
Identity typically refers to how a user logs into various digital resources, and the most common type of identity is a username/password credential set. However, this is only a single factor of authentication. If someone were to compromise my credentials, they could log in and the security logs would show it was me. This is why multi-factor authentication (MFA) is so critical, as it requires users to have something they know (username/password) but also another factor like a push notification or biometric scan to confirm the individual user more accurately.
Implementing MFA is not just a good security practice but also an absolute requirement for most compliance standards and cybersecurity insurancepolicies. In fact, the Department of Homeland Security (DHS), in conjunction with the Cybersecurity and Infrastructure Security Agency (CISA) and the White House, published security practice guidelines that emphasize the importance of MFA. Enforcing application access based on identity is critical to providing secure access from anywhere.
And still, access is only the beginning; secure connectivity is also key. Likewise, MFA is critical but, if layered on top of a vulnerable connectivity solution like a VPN or a legacy Zero Trust Network Access (ZTNA) product, it cannot protect all applications and can still allow for lateral network movement. With identity-based connectivity, controls for who can access your applications also extend to how they connect. This ensures users have a secure, direct connection to the applications they need without receiving risky network access – all regardless of where either the application or the user is located.
At Cyolo, we provide the first and only identity-based access control platform that fully abides by the zero-trust security framework.
All users are validated using industry best practices, like MFA
Each user is only presented with the applications of services they are entitled to
A full audit trail is captured for forensic and compliance needs
We believe that everyone deserves a future where the riskiest attack surface, our people, can safely connect to work.

Author
Josh Martin is a security professional who told himself he'd never work in security. With close to 5 years in the tech industry across Support, Product Marketing, Sales Enablement, and Sales Engineering, Josh has a unique perspective into how technical challenges can impact larger business goals and how to craft unique solutions to solve real world problems. Josh joined Cyolo in 2021 and prior worked at Zscaler, Duo Security, and Cisco.
Outside of Cyolo, Josh spends his time outdoors - hiking, camping, kayaking, or whatever new hobby he's trying out for the week. Or, you can find him tirelessly automating things that do NOT need to be automated in his home at the expense of his partner. Josh lives in North Carolina, USA.

