How Zero Trust Protects Your Source Code And Production Environment: 3 Use Cases

Written By
Eran Shmuely


Written By

Your developers and DevOps engineers have access to your most valuable product property: your source code and production environments. However, vulnerabilities on developer’s devices and manual errors can lead to wide-scale cyber attacks. Your entire venture could be at risk. This blog post will explain how to protect your code and product with zero trust, through three developer-focused use cases.
When a major bug in production occurs, developers have to immediately jump on board to debug, fix and release again. If they are not in the office, they might not have access to production through their home IP or any public IP they’re connecting from.
This will typically require them to whitelist their current IP address by logging into the cloud provider, make changes to a security group and then connect. Sometimes, they might forget to delete the policy or rule that enabled them to connect from home or the public place they were at, like StarBucks.
This manual error leads to a vulnerability, enabling cyber criminals to access the system. These bad actors use scanners, such as shodan.io, to detect publically accessible systems at scale and use automated tools to try and gain unauthorized access.
A zero trust access policy is typically based on identities which only allows authenticated users and devices to access the network, no matter where they are: at work, at home, at StarBucks or on a plane. By implementing zero trust, developers can access production and all environments without having to change the company’s security policies. If the device is registered in the system, the IP it’s connecting from does not matter. Thus, zero trust protects the network and mitigates the risk of enlarging the attack surface that occurs when opening up the security policies.
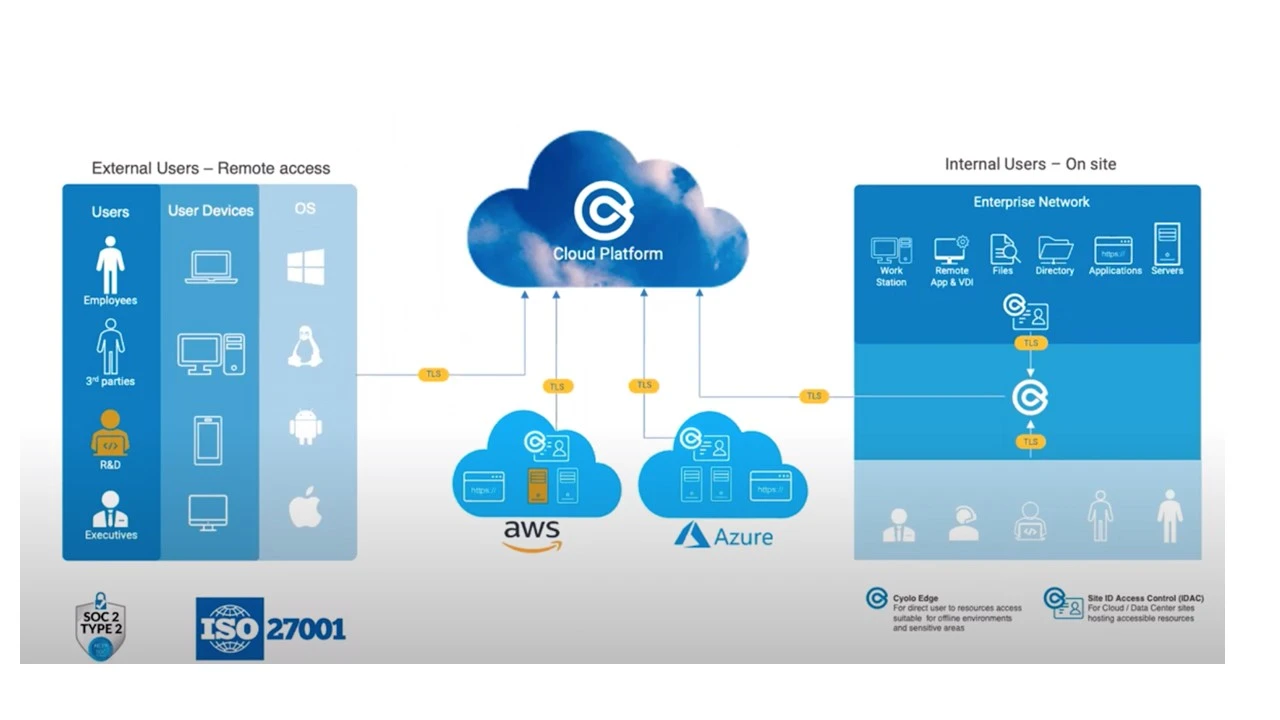
Zero trust is based on identity and device authentication. But what happens when malware is injected on the device? An authenticated device might actually become an insider threat, by allowing the perpetrator access to the crown jewels through its own authentication method!
Source code is dispersed across multiple devices, Therefore, first of all it is recommended to ensure that the developer’s hard disk is encrypted and their system is protected by an up-to-date antivirus software. These measures make it harder for bad actors to access the source code on developers’ computers.
Cyolo’s zero trust authentication method is based on two step verification.
Step 1: The device uploads a trusted CA certificate from the root CA
Step 2: The certificate is authenticated through a 3rd party inventory service like SCCM or BigFix
After the Cyolo connector verifies the certificate through a query to an inventory service, as well as the health of the device and the fact the device has an encrypted hard drive – access is granted.
This prevents the malware on the device from falsifying the authentication and giving itself access.
Nowadays, it can be difficult to upkeep and maintain security policies and user permissions for various platforms and firewalls. Thus, irritated employees, or even just former employees, might have access to source code and production environments. This access could lead to accidental or intentional data breaches, threats and attacks.
Zero Trust enables:
Updating user permissions easily and clearly
Continuous validation of users
Recording and auditing abilities
Monitoring abilities
Most importantly, once the user’s account is disabled in the identity provider, their access is automatically revoked from all systems, apps and everything else.
These ensure CISOs and security admins have control over the users, as well as visibility into network traffic and which actions users are taking inside. Former employees will be blocked from accessing valuable apps and assets, and their actions in the network will be seen and monitored.
Developers and DevOps engineers are the backbone of your product. But even they are prone to manual errors and vulnerabilities. Implement Zero Trust Architecture easily and protect your most valuable product assets: your source code and production environments.

Author
Eran Shmuely is the Chief Architect and Co-Founder of Cyolo. Prior to Cyolo, Eran was the Senior Security Engineer at Salesforce and the Open-Source Security Research Leader at GE Digital.

