Cyolo PRO for Oil & Gas
The oil and gas (O&G) sector provides vital resources that enable countless other industries to operate and allow society as we know it to function. Unfortunately, an increasing number of adversaries also recognize the value of the O&G sector. These threat actors are accelerating their attacks on industrial control systems (ICS) and other operational technology (OT) in order to disrupt operations, commit espionage, and generally wreak havoc.
At the same time, remote work, automation, progress toward Industry 4.0, and rising connectivity between operational technology (OT) and information technology (IT) are creating new opportunities as well as new vulnerabilities for O&G companies.
Remote connectivity, as one example, reduces costs, improves operational agility, and lowers safety risks by enabling maintenance on offshore drilling rigs or distant oil fields to be conducted without traveling to these far-off locations. However, remote access creates its own security and safety risks.
If proper access, connectivity, and supervisory controls are not in place, a security incident could potentially occur at any point across the three major stages of O&G operations: upstream, midstream, or downstream. Attacks could be the result of espionage, cyber-terrorism, ransomware gangs seeking a quick, high-value payout, or critical cybersecurity vulnerabilities affecting the aging infrastructure and legacy systems that characterize OT environments.
And the stakes simply could not be higher when it comes to protecting O&G facilities and the critical infrastructure within them. A cyberattack against these targets could cause immense damage, including financial loss and economic disruption, threats to human safety and the environment, and even the destabilization of nation states.
Cyolo PRO (Privileged Remote Operations) is an advanced Secure Remote Access solution that empowers O&G organizations to safely connect remote workers, third-party vendors, and privileged employees to even the most sensitive assets and environments.
Rising Connectivity, Rising Risks
The O&G industry is deeply dependent on systems that are becoming more digitally connected. Connectivity lowers costs, increases efficiency, and decarbonizes the sector, but it also introduces new risks.
Robust cybersecurity will enable O&G companies to fully enjoy the benefits of digital transformation and IT/OT convergence. But there is work to do, as 69% of O&G professionals worry their organization is more vulnerable to cyberattacks now than in the past.
How Oil & Gas Companies are Managing Access and Risk
Just 51% of O&G companies identify securing access to OT environments as a high priority.
74% of O&G companies do not maintain an accurate, up-to-date inventory of the industrial assets in their OT environments.
47% of O&G companies lack confidence that they’re effectively protecting their OT environments.
60% of O&G companies grant OT systems access to more than 50 different vendors, and 25% give such access to more than 100 vendors.
(Source: Ponemon Institute and Cyolo, 2024)
Key Remote Privileged Access Use Cases for the Oil & Gas Industry
Facilitate third-party remote access: Safely connect third-party vendors to OT environments for enhanced productivity.
Provide OEM access for fast, secure support: Ensure rapid, secure, and safe support and maintenance of diagnostics (M&D) for OT systems.
Manage critical and risky access: Secure, monitor, and control all connections to mission-critical assets, whether on-premise or remote.
Achieve regulatory compliance: Implement segmentation, supervision and other requirements of industry and regional compliance mandates.
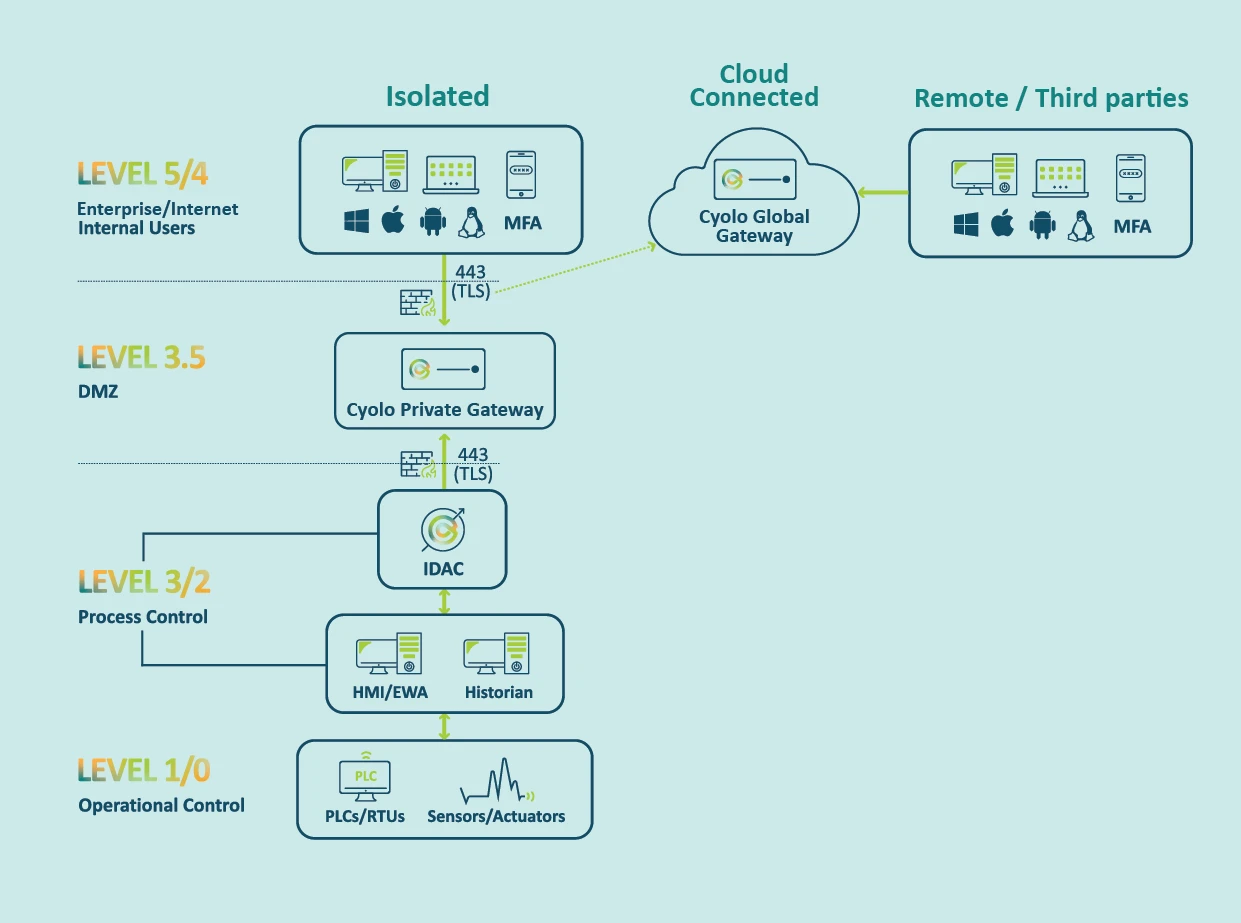
Cyolo PRO: A Single Unified Solution with 3 Security Layers
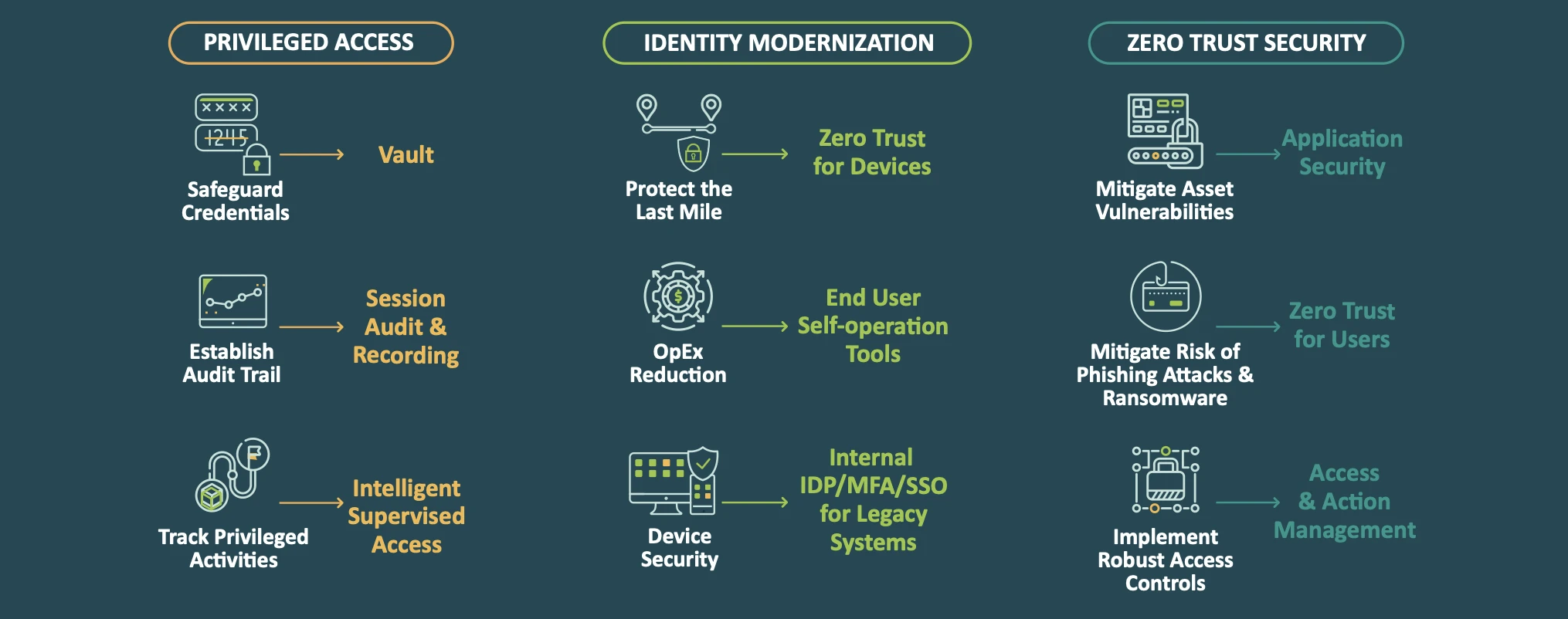
Cyolo PRO's Unique Architecture Enables Maximum Flexibility
The light and adjustable Cyolo component can fit into any infrastructure or environment and always keeps your data safe and secure within your trusted boundaries.
Even in cloud-connected environments, data is routed only in an encrypted state, ensuring low latency and high levels of security.
Cyolo PRO Benefits
Security
Keep your data inside your trusted boundaries
Granular identity-based controls & supervision
Full activity/audit trails
Flexibility
Deploy on-premise, on-cloud & hybrid — simultaneously
Extend identity authentication and security to legacy applications
Centralized governance & site-based administration
Simplicity and Ease of Use
Agentless deployment
Consolidated access controls with modularity
Low-latency/High-availability
Intelligent supervision eases operational burden
Case Study: How a Leading Energy Provider Ensures Secure Access to OT and SCADA Systems
The Need
Remotely connect global partners and third-party suppliers to critical systems
Top Challenges
Required a single solution to enable secure access for global support teams, third-party suppliers, and customers
Needed to meet strict internal and external security regulations
Sought to reduce friction and improve user experience for frustrated employees and support teams
Business Outcomes
Fastest deployment in company history
Fast, secure, and seamless access for all users to IT, OT, and SCADA systems
Months of work reduced to hours
Hundreds of thousands of dollars saved, plus significantly reduced travel costs
Improved productivity and user satisfaction
About Cyolo
Cyolo provides secure remote privileged access for cyber-physical systems (CPS). Our solution enables industrial enterprises to simply connect employees and third-party vendors to critical assets.
Cyolo meets the needs of security and operational technology (OT) teams with a solution that’s adaptable to any environment and deploys without causing disruptions or requiring change management. Cyolo delivers improved security, productivity, and operational agility – without compromise.
Schedule a personalized demo to see the Cyolo PRO access solution in action.

Subscribe to Our Newsletter







