Cyolo PRO for Smart Manufacturing
The advent of Industry 4.0 has revolutionized manufacturing operations by integrating cutting-edge technologies such as automation, Internet of Things (IoT), and data analytics into traditional industrial processes. However, increased connectivity between operational technology (OT) and information technology (IT) has significantly heightened cybersecurity risks in manufacturing environments. According to recent Ponemon Institute research, as many as 72% of manufacturing organizations are currently pursuing some level of IT/OT convergence.
With interconnected systems and devices forming the backbone of smart factories, the attack surface for cyber threats has expanded exponentially. Increased connectivity and data visibility within the manufacturing ecosystem make it a prime target for cyberattacks, with the sector experiencing the highest number of attacks globally for three consecutive years, comprising 25.7% of all attacks.
Cyolo PRO (Privileged Remote Operations) is an advanced secure remote access solution that empowers manufacturers to safely connect remote workers, third-party vendors, and privileged employees to even the most sensitive assets and environments.
Manufacturing Cybersecurity: Statistics and Risks
Rising Cybersecurity Incidents: Over 60% of manufacturing companies have experienced cyberattacks, reflecting an escalating risk environment.
Financial Ramifications: The average cost of a cyber breach in this sector is around $1 million, signifying substantial financial risks.
IoT Expansion and Risks: IoT integration exposes new risks, leading to 30% increase in security incidents.
Human Error: Internal vulnerabilities, primarily due to human error, account for 70% of breaches in manufacturing, underscoring the importance the comprehensive cybersecurity training.
(Source: DataGuard, 2024)
Managing Access and Risks in Connected OT Environments
45% of security professionals believe their organization is not effectively mitigating risks and security threats to the OT environment.
73% of industrial organizations do not maintain an accurate, up-to-date inventory of the assets in their OT environment.
60% of industrial organizations grant OT systems access to more than 50 different vendors, and 25% give such access to more than 100 vendors.
72% of industrial organizations are pursuing some level of IT/OT convergence, but just 33% have policies, tools, governance and reporting in place to control and monitor connectivity between IT and OT systems.
(Source: Ponemon Institute and Cyolo, 2024)
Key Remote Privileged Access Use Cases for the Manufacturing Industry
Facilitate third-party remote access: Safely connect third-party vendors to OT environments for enhanced productivity.
Provide OEM access for fast, secure support: Ensure rapid, secure, and safe support and maintenance of diagnostics (M&D) for OT systems.
Manage critical and risky access: Secure, monitor, and control all connections to mission-critical assets, whether on-premise or remote.
Achieve regulatory compliance: Implement segmentation, supervision and other requirements of industry and regional compliance mandates.
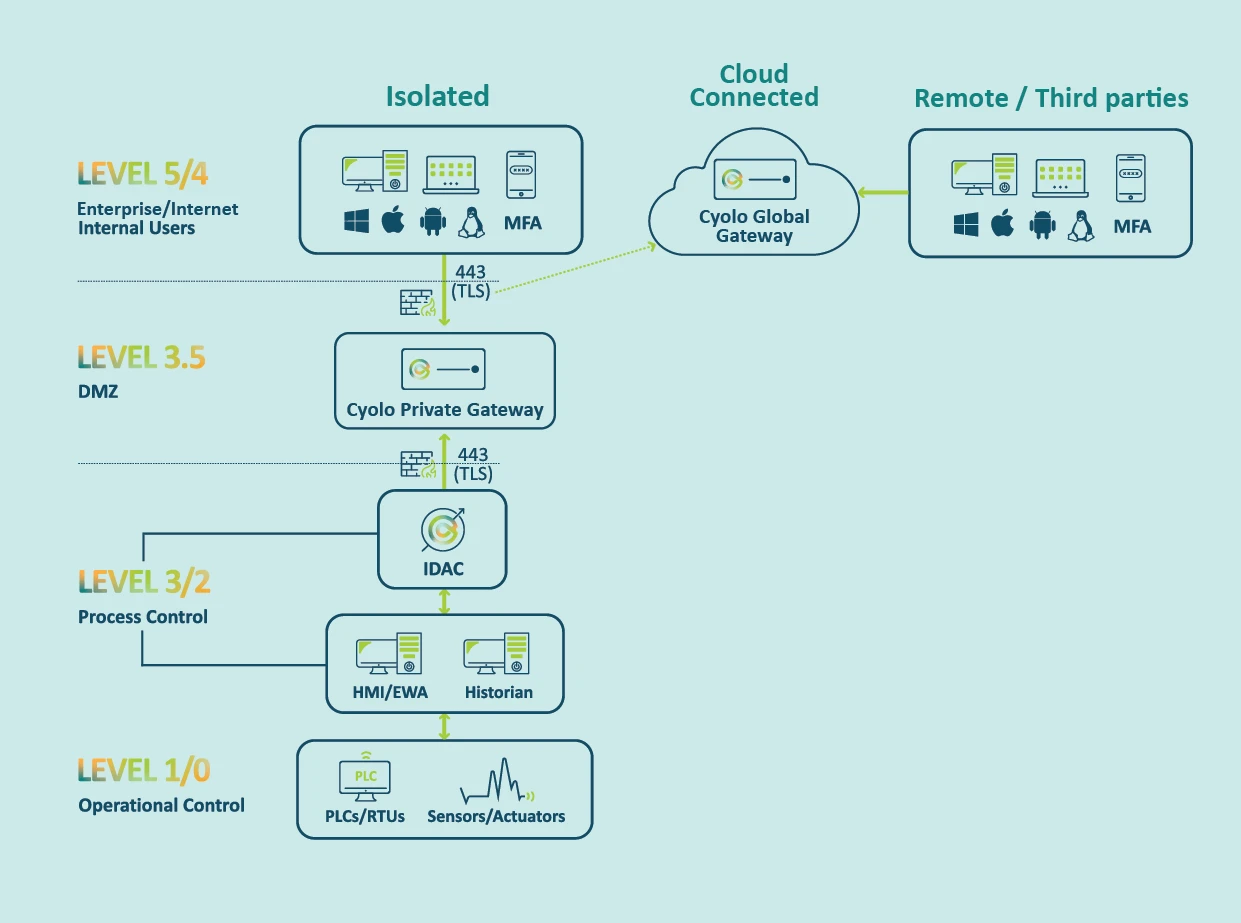
Cyolo PRO: A Single Unified Solution with 3 Security Layers
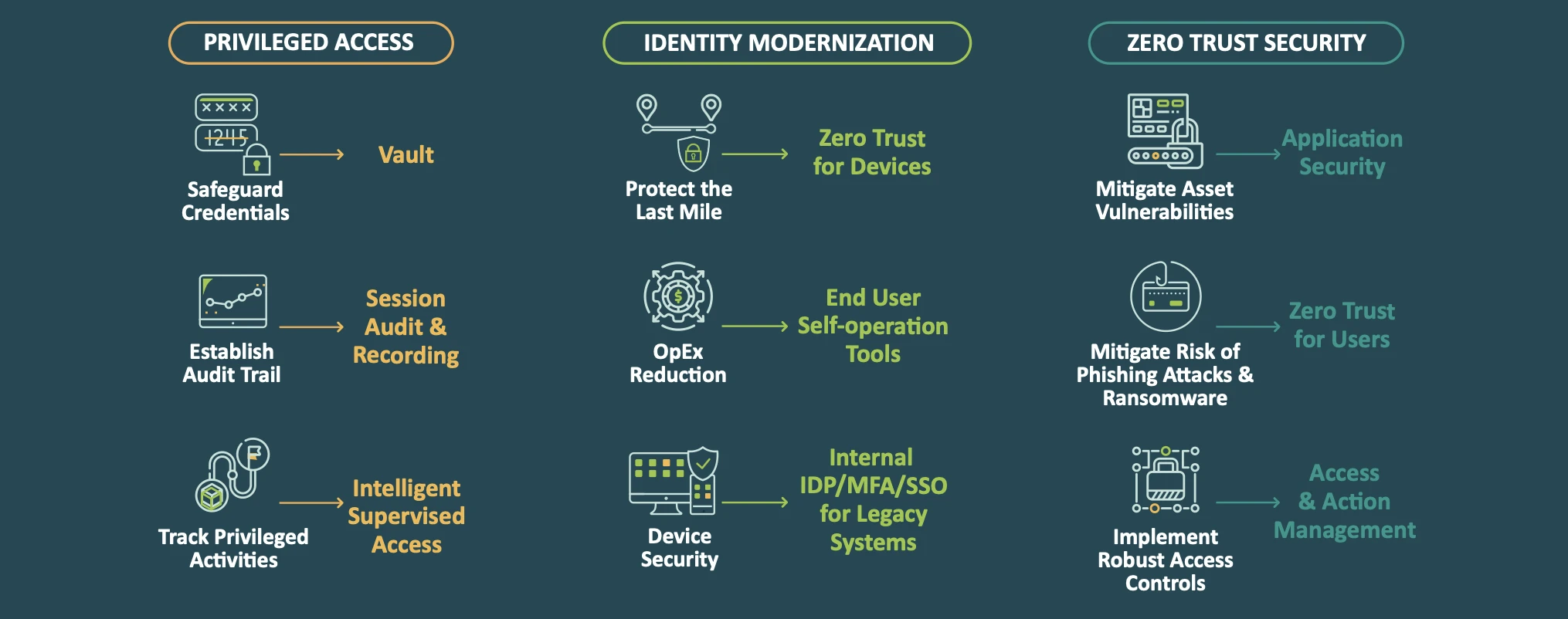
Cyolo PRO's Unique Architecture Enables Maximum Flexibility
The light and adjustable Cyolo component can fit into any infrastructure or environment and always keeps your data safe and secure within your trusted boundaries.
Even in cloud-connected environments, data is routed only in an encrypted state, ensuring low latency and high levels of security.
Cyolo PRO Benefits
Security
Keep your data inside your trusted boundaries
Granular identity-based controls & supervision
Full activity/audit trails
Flexibility
Deploy on-prem, on-cloud & hybrid — simultaneously
Extend identity authentication and security to legacy applications
Centralized governance & site-based administration
Simplicity and Ease of Use
Agentless deployment
Consolidated access controls with modularity
Low-latency/High-availability
Intelligent supervision eases operational burden
Case Study: Global Top 3 Food and Beverage Manufacturer
The Customer
100 global sites
2000 remote maintenance and support engineers
The need: Simplify secure access for third parties to the factory floor
Top Challenges
Complex login processes on both the user side (7 logins for an RDP!) and admin side (excessive ticketing)
Needed secure file transfer within the OT environment
Needed to allow emergency fix access for an OEM vendor
Business Outcomes
Simple, secure, and agentless remote access for employees, third-party contractors, and OEM vendors
File scanning (ICAP) integration within the policy
No need to change existing network topology
Fast and secure remote OEM support
Deployment in under 90 days
About Cyolo
Cyolo provides secure remote privileged access for cyber-physical systems (CPS). Our solution enables industrial enterprises to simply connect employees and third-party vendors to critical assets.
Cyolo meets the needs of security and operational technology (OT) teams with a solution that’s adaptable to any environment and deploys without causing disruptions or requiring change management. Cyolo delivers improved security, productivity, and operational agility – without compromise.
Schedule a personalized demo to see the Cyolo PRO access solution in action.

Subscribe to Our Newsletter







