Table of Contents
Introduction
In the dynamic realm of Cyber-Physical Systems (CPS), ensuring secure remote access (SRA) is critical to balancing stringent security requirements with operational efficiency. Traditional solutions like VPNs, jump servers, and cloud-hosted remote access tools often necessitate significant network modifications that can inadvertently introduce new attack surfaces or store sensitive user data externally.
Effective SRA solutions should minimize metrics such as mean-time-to-detection (MTTD) and mean-time-to-respond (MTTR). By facilitating rapid diagnosis and targeted responses, these solutions enhance remediation efforts and reduce the lead time to protection. For instance, enabling direct login access to devices like building automation control sensors, building management systems, and video monitors allows operators to gain real-time insights into physical environments. This capability is crucial for promptly addressing incidents — for example, accessing a door control system to investigate and remediate unauthorized access attempts using biometric data.
However, many traditional SRA tools are incapable of reaching Purdue Model Level 2 environments — where critical access may be required — without exposing sensitive networks to the internet. This exposure conflicts with the secure network design principles outlined in the ISA/IEC 62443 standards, which advocate for robust segmentation and defense-in-depth strategies to protect industrial automation and control systems. Moreover, relying on jump servers to facilitate such access not only increases complexity and cost but also expands the attack surface, further compromising security.
Cyolo takes a different approach by providing a distinctive decentralized architecture that ensures security, adaptability, and compliance without requiring any network reconfiguration.
Cyolo’s Unique Approach to Secure Remote Access
Cyolo’s architecture is built around two core components: the Cyolo Gateway and the IDAC (Identity and Access Controller). The Gateway’s sole function is Server Name Indication (SNI) routing, while the IDAC, deployed entirely within the customer’s environment, ensures that sensitive data and authentication remain on-premises. Unlike legacy VPNs that connect users to networks, Cyolo connects secure identities only to approved applications instead of users to entire networks.
Gateway Chaining: Securely Extending Access Without Compromising OT Networks
One of Cyolo’s key differentiators is its ability to chain gateways with no limitations, enabling seamless scalability and flexibility for organizations. This unparalleled feature ensures that businesses can securely connect users to critical systems and applications, regardless of their location or infrastructure complexity. By eliminating constraints typically associated with traditional gateway solutions, Cyolo empowers companies to adapt quickly to evolving operational needs while maintaining robust security and performance.
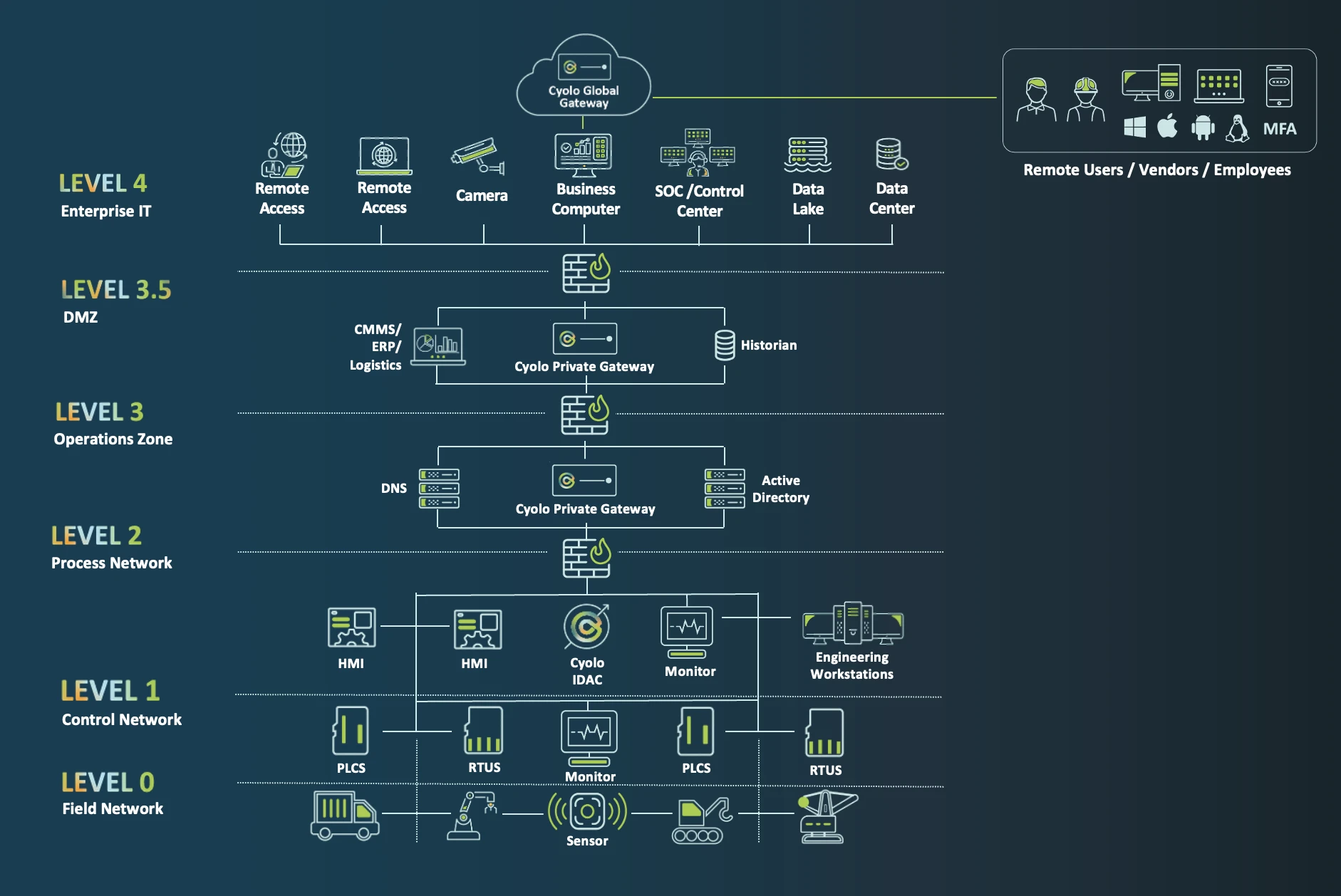
This unique capability allows organizations to place the IDAC at Purdue Level 2, closest to critical OT assets, while only requiring a single outbound TLS 443 connection in existing firewalls at each layer to the chained Cyolo Private Gateways. This architecture enables Cyolo PRO to seamlessly adapt to any network segmentation configuration, ensuring secure and efficient access without necessitating changes to existing infrastructure.
Granular Security Controls: A layered approach minimizes potential attack surfaces, enhances overall network security, and provides administrators with granular control over data flow and access permissions across different network segments. By isolating trust boundaries, Private Gateways also enable compliance with regulatory standards and facilitate the implementation of zero-trust security models, ensuring that each interaction is verified and authorized.
Minimized Firewall Rule Changes: Rather than opening multiple ports across different Purdue levels, Cyolo’s solution requires only a single TLS 443 rule in the organization's existing firewalls. This simplifies deployments, removes complicated firewall rules for legacy solutions and significantly reducing the attack surface.
Adaptability for Isolated and Hybrid Environments: Organizations can implement multiple on-premises gateways to securely route traffic between Level 2 and Level 4, ensuring no direct exposure to external networks.
Cloud-Routed, Not Cloud-Hosted: Enhancing Security and Compliance
Many secure remote access solutions require a cloud-hosted management architecture that introduce potential security concerns by storing authentication and session data externally. Cyolo, in contrast, is cloud-routed rather than cloud-hosted. This distinction means:
Customer Data Stays On-Prem: Authentication and user session details remain entirely within the customer’s infrastructure, preventing unauthorized data exposure.
No Third-Party Data Storage Risks: Unlike traditional cloud-based solutions, Cyolo’s model ensures that even in cloud-connected deployments, sensitive OT assets are never exposed to external environments.
Compliance with Stringent Industry Regulations: Compliance with stringent industry regulations is paramount for organizations operating Cyber-Physical Systems (CPS). By keeping all data within the customer’s domain, Cyolo helps organizations meet strict regulatory requirements, such as NIST 800-171, NIS2, and ISA/IEC 62443, while benefiting from a flexible and scalable remote access solution.
Seamless Integration Without Network Re-Architecting
A major challenge with many secure remote access solutions is the need for extensive network reconfiguration to accommodate new security controls. Cyolo is designed to work within an organization’s existing network infrastructure, providing:
Deployment Without Disruptions: The flexibility of chaining Cyolo gateways allows organizations to maintain their existing network architecture while introducing a secure remote access solution.
Scalability Without Complexity: Whether in cloud-connected, hybrid, or air-gapped environments, Cyolo adapts to the existing network topology, eliminating the need for costly re-architecting.
Uninterrupted Operations: Unlike VPNs and jump servers that introduce latency and complexity, Cyolo enables seamless remote access with minimal impact on operational continuity.
Conclusion
Cyolo’s unique approach to secure remote access revolutionizes how OT environments implement secure connectivity. By offering unlimited gateway chaining, a cloud-routed or strictly air-gapped model rather than cloud-hosted model, and seamless integration into existing network infrastructures, Cyolo ensures that organizations achieve the highest level of security without compromising operational efficiency. In a world where secure remote access is critical, Cyolo provides a solution that is not only secure and compliant but also flexible and scalable for the future.
Discover the Benefits of Cyolo PRO (Privileged Remote Operations)

Subscribe to Our Newsletter







