Table of Contents
- The State of Industrial Secure Remote Access (I-SRA)
- 3 Key Trends in Industrial Secure Remote Access
- 1. Third-Party Access is the Top Reason for Enabling I-SRA
- 2. I-SRA is Not Just a “Big Company” Problem
- 3. Across All Industries, Concerns Outweigh Confidence
- Discover the Full Scope of I-SRA Needs and Challenges
- About Takepoint Research
- About Cyolo
The State of Industrial Secure Remote Access (I-SRA)
Remote access has become a universal and fundamental requirement for most industrial enterprises. But just enabling remote access is far from sufficient; it is equally crucial that these connections are secure. Approaching industrial secure remote access (I-SRA) from a position of “connect first, secure later” is a recipe for abuse by malicious actors and a clear threat to operational safety.
Most security tools commonly applied to OT environments were originally designed for information technology (IT), and fail to consider the everyday realities of OT. At the same time, a lack of protocol standardization in the operational technology (OT) realm creates a huge disparity among OT environments, making it difficult for a single solution to cover the entire range of an organization’s use cases. In short, there is no widely applicable framework or playbook for securing remote access. Each organization is left to figure it out for themselves.
This is why we at Cyolo sponsored a new research report by Takepoint Research: The State of Industrial Secure Remote Access.
OT, engineering, IT, and cybersecurity professionals were surveyed for the report in the first quarter of 2023, with the aim of better understanding the challenges of successfully enabling and securing remote access to industrial environments.
3 Key Trends in Industrial Secure Remote Access
1. Third-Party Access is the Top Reason for Enabling I-SRA
Across all industries, third-party access ranked as the number-one reason for securing remote access (selected by 72% of respondents).
This isn’t too surprising, as OT environments tend to depend heavily on third parties due to a significant skills gap, original equipment manufacturer (OEM) maintenance requirements, risk mitigation, among other factors.
In the past, OT and industrial control systems (ICS) technologies were fully isolated from the internet or other connections, and only a select cadre of technicians knew how to build, manage, and maintain these systems. With just a small number of highly-skilled hands ever touching them, the potential for damage to these systems was limited. Today, the situation is very different. Information about these systems has become easily accessible for malicious actors, and IT/OT convergence — which creates new entry points into OT environments — is accelerating.
In many ways, these changes have caught the OT world on its heels. The teams responsible for security often don’t even know how many internal users, external users, and back doors are present in their systems. Likewise, a lack of session monitoring or recording solutions creates visibility gaps for attackers seeking to exploit these sensitive systems.
2. I-SRA is Not Just a “Big Company” Problem
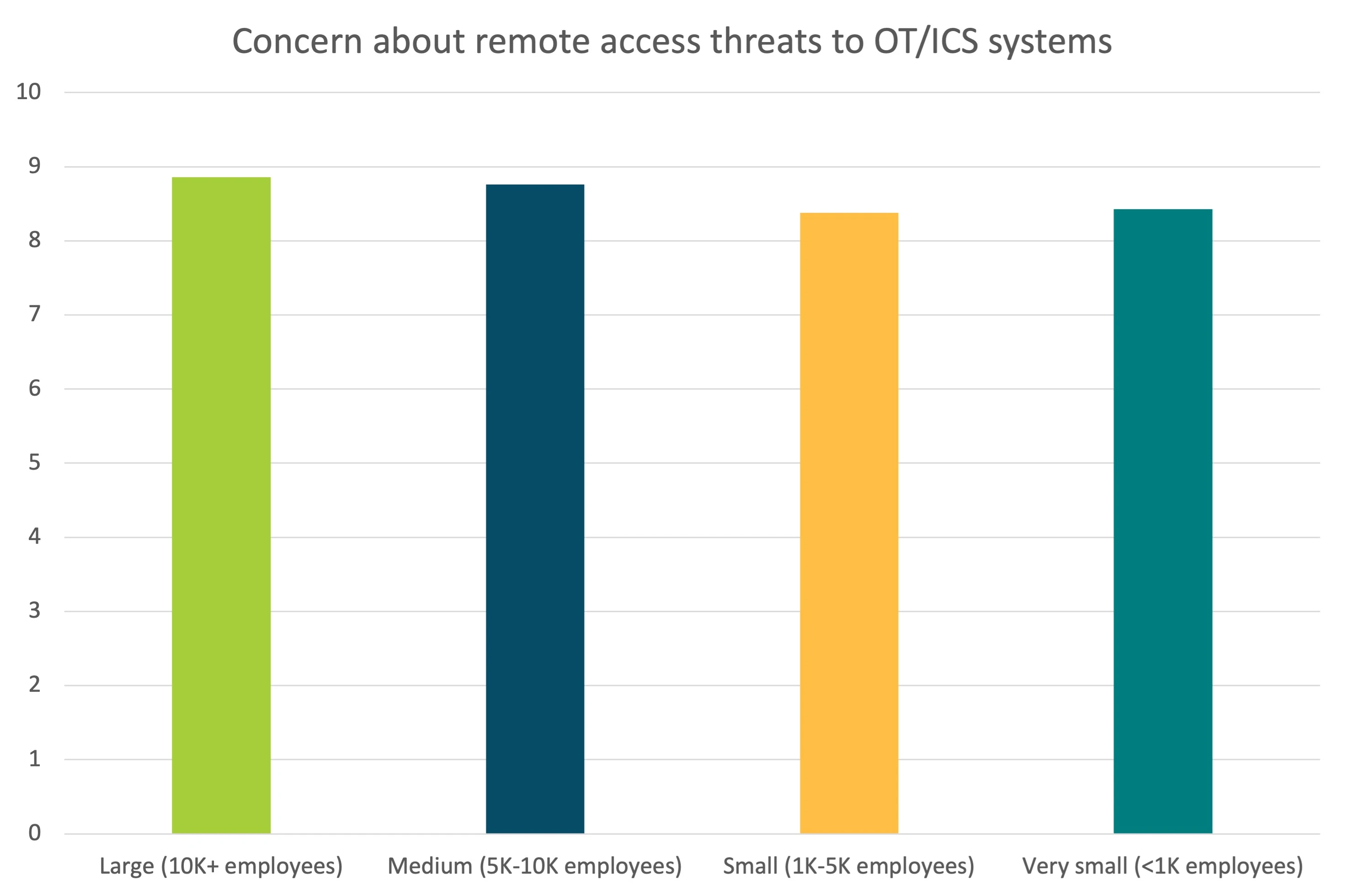
The Takepoint report reveals a linear relationship between company size and the sheer volume of remote connections: the bigger the company, the more connections. It’s tempting to conclude that smaller companies with fewer connections (and thus a smaller attack surface) are more secure.
However, the data paints the opposite picture.
The level of concern around remote access risks was actually consistent from the smallest to largest companies. Professionals at smaller companies were no less worried about remote access vulnerabilities than those at larger companies.
Although larger companies naturally have a larger attack surface to secure, they are also more likely to have teams robust enough to do so. Small companies, meanwhile, may lack the budget, headcount, and experience necessary to adequately defend their systems.
While attacks against big-name organizations typically grab the most prominent headlines, small businesses should not assume they’re flying under the radar.
46% of breaches occur at businesses with fewer than 1,000 employees.
Phishing accounts for 85% of cyber threats to manufacturing businesses, and small businesses receive the highest rate of targeted malicious emails.
A cybersecurity incident at a small business costs around $200,000 on average.
3. Across All Industries, Concerns Outweigh Confidence
Perhaps the most striking finding of the survey: Across all industries, respondents were more concerned about threats than confident in their current I-SRA solutions.
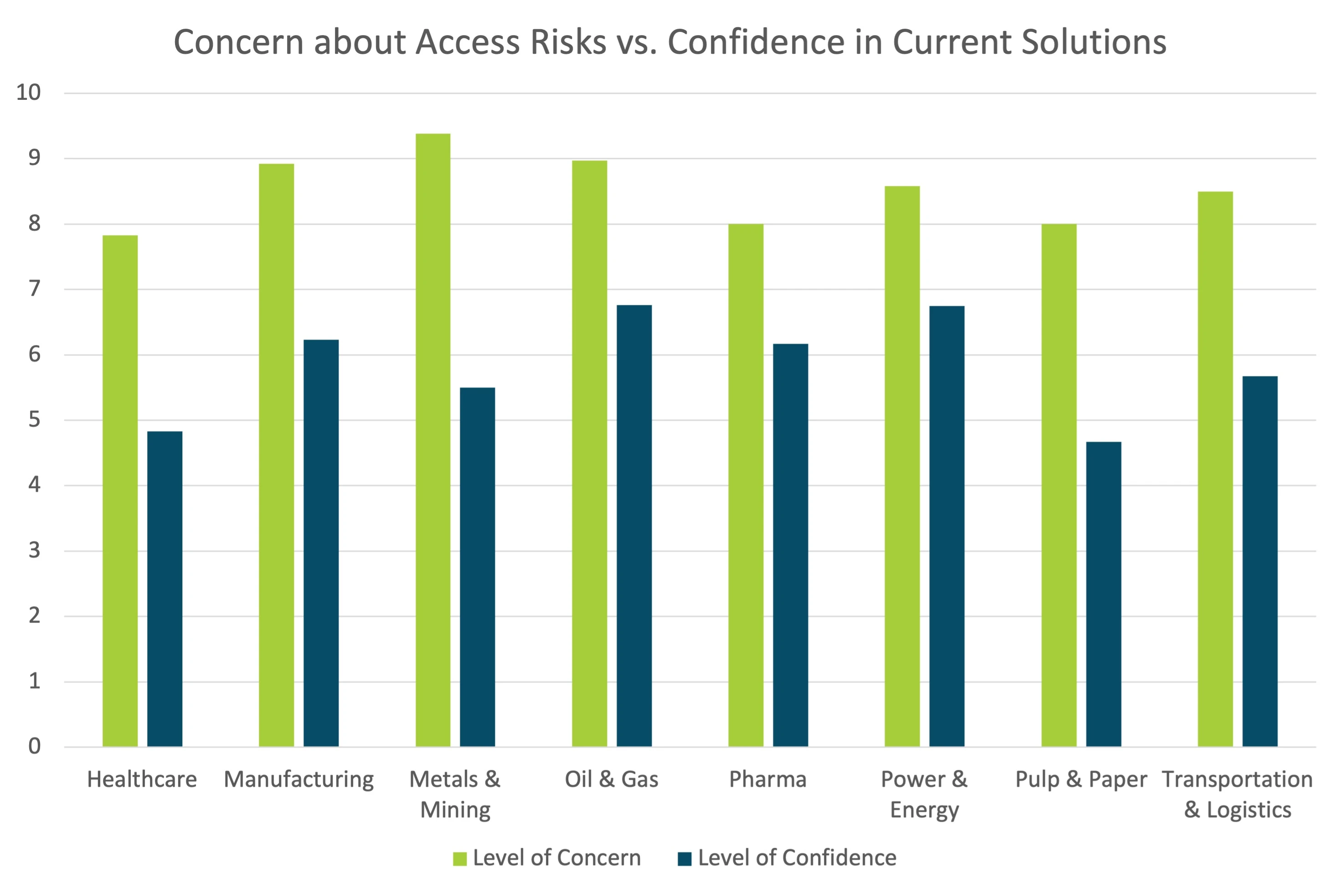
Industrial settings have built brittle workarounds for securing remote access, like firewalls and Virtual Private Network (VPNs), and have sought to implement frameworks like NIST 800-82 or ISA/IEC62443. Still, they recognize that the problem is not solved.
Simply put, teams allow remote access to their critical systems because operations depend on it – but that access is far less secure than they’d like.
Compromised credentials present an easy access point for hackers, because existing I-SRA tools don’t secure the user’s identity.
Commonly used SRA solutions like VPNs struggle to scale and cannot cover the full range of OT use cases.
Due to a lack of SRA solutions built specifically for OT, there’s a frequent need to rely on tools designed for IT. These are far from ideal because they often require a cloud connection, need regular patching that requires downtime, or interrupt sensitive OT processes.
Discover the Full Scope of I-SRA Needs and Challenges
The precise reasons for needing I-SRA vary across industries and regions, but a clear commonality prevails: Industrial organizations need the ability to provide remote access, and they are seeking out solutions and strategies to make that access more secure.
For a more complete look at how companies and security experts around the world are approaching the challenges of secure remote access, download the full report.
About Takepoint Research
Takepoint Research (TPR) is a boutique industry analyst firm that provides focused research and actionable insight for industrial enterprises and those tasked with protecting them from cyber threats. TPR resources and analysis help them make informed decisions about evolving their industrial cybersecurity programs to meet the changing threat landscape. Collaboration is at the heart of our model and our mission is simply to deliver expert insight that has tangible value for your company.
About Cyolo
Too many critical assets and systems remain exposed because traditional secure access solutions are unable to protect the high-risk access scenarios and legacy applications that power modern business operations.
Founded by a former manufacturing industry CISO and two ethical hackers, Cyolo was created to solve the challenge of securely connecting high-risk users, including remote workers and third-party contractors, to mission-critical applications within every kind of environment (on-premises, on IaaS platforms, and hybrid).
Cyolo is setting a new standard for secure remote access by providing an advanced solution purpose-built to give industrial organizations visibility and control over the users who leave them most exposed to risk.

Jennifer Tullman-Botzer
Author
Jennifer Tullman-Botzer has over a decade of experience in cybersecurity marketing and is as tired as you are of hackers-in-hoodies stock images. She joined Cyolo in 2021 and currently serves as director of content marketing.

Subscribe to Our Newsletter







