Table of Contents
Securing Remote Access is an Ongoing Challenge
In an age where remote work is accepted practice but cyberthreats are rising, organizations must be able to ensure that remote users are accessing internal systems and resources without creating vulnerabilities or increasing risk. It is particularly important to enable secure access for privileged users, a group that includes not just admins with elevated access permissions but also third-party vendors, technicians, and contractors, and other workers who connect remotely to sensitive data and critical systems.
A variety of solution categories exist to help extend secure access to remote users who pose substantial risk, including Secure Remote Access (SRA), Zero Trust Network Access (ZTNA), and Privileged Access Management (PAM). However, even with a wealth of secure access and privileged access solutions on the market, a recent Gartner® report entitled Securing Remote Privileged Access Management Through RPAM Tools states, “many organizations are finding it increasingly difficult to implement robust controls that monitor, govern and establish better audit trails to track privileged activities of remote users leading to administration and governance oversight.”1
A new solution class, Remote Privileged Access Management (RPAM), is emerging to solve this challenge. RPAM tools offer greater access control than PAM solutions and greater connectivity and oversight controls than SRA or ZTNA solutions.
What is RPAM?
Despite its name, RPAM is not a version of PAM but rather a wider concept about how access is provided, managed, and controlled for privileged remote users.
With an RPAM solution in place, access is granted only to verified identities according to the principle of least privilege, and even authenticated users or devices can be restricted from performing risky actions. This and other controls around access, connectivity, and oversight help to lower risk and reduce the organizational attack surface. At the same time, RPAM also increases administrative efficiency and operational agility by easing the burden placed on IT and security teams.
Key Features of RPAM
Gartner divides the key features of RPAM into 4 areas, as seen in the image below.
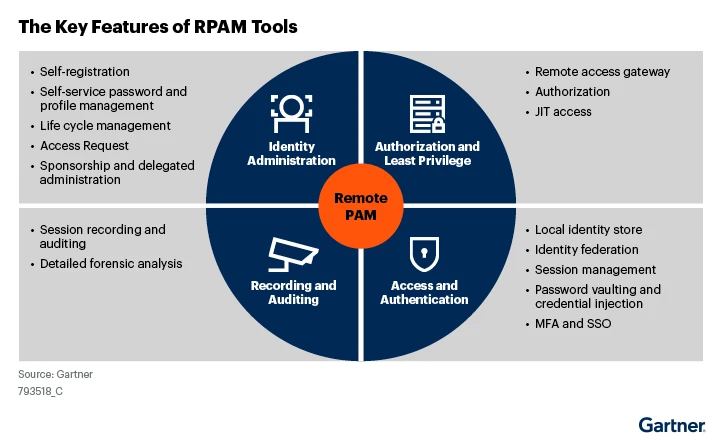
Features related to authorization and least privilege limit visibility to authorized resources only, enable secure access for shared accounts, and permit just-in-time access bound by time and other parameters.
Access and authentication features can be used to manage the identities of remote privileged users, leverage identity federation, and conduct session management in real-time. Password vaulting and enforcement of multi-factor authentication (MFA) augment security and help prevent unauthorized access
Recording and auditing allow for greater oversight of privileged activities and are required by many regional and industry-specific compliance mandates.
Identity administration features like self-registration, self-service password renewal, and lifecycle management take pressure off IT and security teams, improving user experience as well as operational agility.
Simply put, a robust RPAM solution will allow organizations to more effectively manage the entire lifecycle of a privileged remote connection – from the initial verification of identity through to the termination of the session. Organizations using RPAM will also be well-positioned to meet compliance regulations that mandate MFA, zero-trust access, secure access for third-party vendors, session recording, and more.
Who Should Use RPAM?
RPAM can be used to secure privileged remote access in any industry or environment, including both information technology (IT) and operational technology (OT). This said, RPAM brings perhaps its biggest benefit to OT environments and Cyber Physical Systems (CPS), which can be difficult to secure with traditional remote access solutions. Many tools designed for the world of IT are difficult to deploy in OT settings or cannot provide their full functionality, and even some access solutions built for OT fail to offer the advanced authentication and oversight capabilities that are at the core of RPAM.
According to Gartner, “most organizations struggle to apply the ‘principle of least privilege’ for their remote privileged access scenarios to cyber-physical systems, leading to less-secure remote access for their privileged external users.” Given the potentially catastrophic consequences of a cyberattack against CPS, coupled with the widespread dependence of industrial enterprises on external third-party vendors, organizations that operate CPS should consider replacing or augmenting their current secure remote access tools with RPAM.
RPAM is the Future of Secure Remote Access
Why secure only the original point of access when you can ensure the ongoing security of the connection? Now is the time to get ahead of the curve and consider RPAM as a solution to the challenge of enabling secure access for privileged remote users.
Gartner predicts that “by 2026, organizations applying least privilege principle approaches to remote privileged access management (RPAM) use cases will reduce their risk exposure by more than 50%.”
To start your journey toward remote privileged access, read this brief about the Cyolo PRO (Privileged Remote Operations) hybrid secure access solution or schedule a demo with a Cyolo expert.
Frequently Asked Questions about RPAM
Remote Privileged Access Management (RPAM) is a cybersecurity approach and set of technologies that secure, control, and monitor elevated access for remote privileged users such as OT operators third-party vendors. Unlike traditional privileged access management (PAM) or secure remote access (SRA) tools, RPAM combines identity-based access control with continuous session governance and oversight capabilities to reduce risk in OT and critical infrastructure environments.
Traditional PAM and RPAM both secure instances of privileged access, but they address different operating models. Traditional PAM focuses on protecting privileged accounts within a trusted internal network, while RPAM is built specifically for remote environments. RPAM enables identity-based, zero-trust privileged access without relying on VPNs or agents, reducing complexity and attack surface while scaling more effectively across hybrid infrastructures. To learn more, read the blog Remote Privileged Access Management (RPAM) is Not PAM.
Core RPAM capabilities include:
Identity verification and MFA before granting privileged access
Least privilege and just-in-time (JIT) access controls
Session brokering and real-time monitoring
Session recording, auditing, and detailed activity logs
Credential vaulting and lifecycle management
For a deeper dive into this topic, read the blog Top 5 Capabilities to Look for in an RPAM Solution.
Any organization with remote users or third-party vendors needing elevated system access should consider RPAM. It’s especially valuable for industries with OT environments and/or hybrid infrastructures, where traditional SRA or PAM tools may struggle to enforce least-privilege principles and detailed oversight.
1 Gartner, Securing Remote Privileged Access Management Through RPAM Tools, Abhyuday Data, Felix Gaehtgens, Michael Kelley, 28 December 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Discover the Benefits of Cyolo PRO (Privileged Remote Operations)

Jennifer Tullman-Botzer
Author
Jennifer Tullman-Botzer has over a decade of experience in cybersecurity marketing and is as tired as you are of hackers-in-hoodies stock images. She joined Cyolo in 2021 and currently serves as director of content marketing.

Subscribe to Our Newsletter







