The manufacturing industry is in the midst of a digital revolution, with Gartner Inc. research showing that 80% of CEOs rely on digital technology investments to help alleviate economic pressures. Unfortunately, these same technologies are under threat from cyber-attackers. A recent survey from Make UK (The Manufacturers Organisation) reveals that almost half of UK manufacturers (42%) have fallen victim to a cyberattack over the last 12 months.
Let’s explore this report in greater detail and uncover the implications of cybersecurity risk on secure manufacturing.
Examining the State of Cybersecurity in Manufacturing
Make UK represents over 20,000 manufacturers and, per its website, “is focused on creating the most supportive environment for UK manufacturers to thrive, innovate and compete.” The Make UK Cyber Security in UK Manufacturing report, released earlier this year, presents a comprehensive view of how cyber risk impacts secure manufacturing across the United Kingdom. The report’s broadest conclusions can be extrapolated to other parts of the world, and perhaps to other industries, as well.
In its survey gathering data for the report, Make UK asked important and pointed questions aimed at identifying the core security challenges manufacturers face and how they are coping with rising threats. According to the report’s executive summary, 95% of respondents say that “cyber security is a necessary function of their operations.” Just under two-thirds (65%) also assert that cybersecurity has grown in importance over the last 12 months.
It is good news that UK manufacturers appear to recognize the need for cybersecurity; however, this is not translating to action at the rate one might expect. Over half (54%) of respondents reported deciding not to take any further cybersecurity action when adopting new technologies. What could account for this gaping discrepancy?
Words vs. Action in Secure Manufacturing
If respondents admit that cybersecurity is key to combatting increasing levels of risk, why would so many of them simultaneously decide to take “no further action”? The report concludes that there is a “confidence gap between UK manufacturers knowing that cyber security is of paramount importance to their businesses, but [being] less certain in just how
those risks present themselves and subsequently what the best forms of defence are for a given risk.”
A survey on industrial secure remote access, conducted in early 2023 by Cyolo and Takepoint Research, found a similar result, with respondents being significantly more concerned about cyberthreats than they are confident in their existing access security solutions.
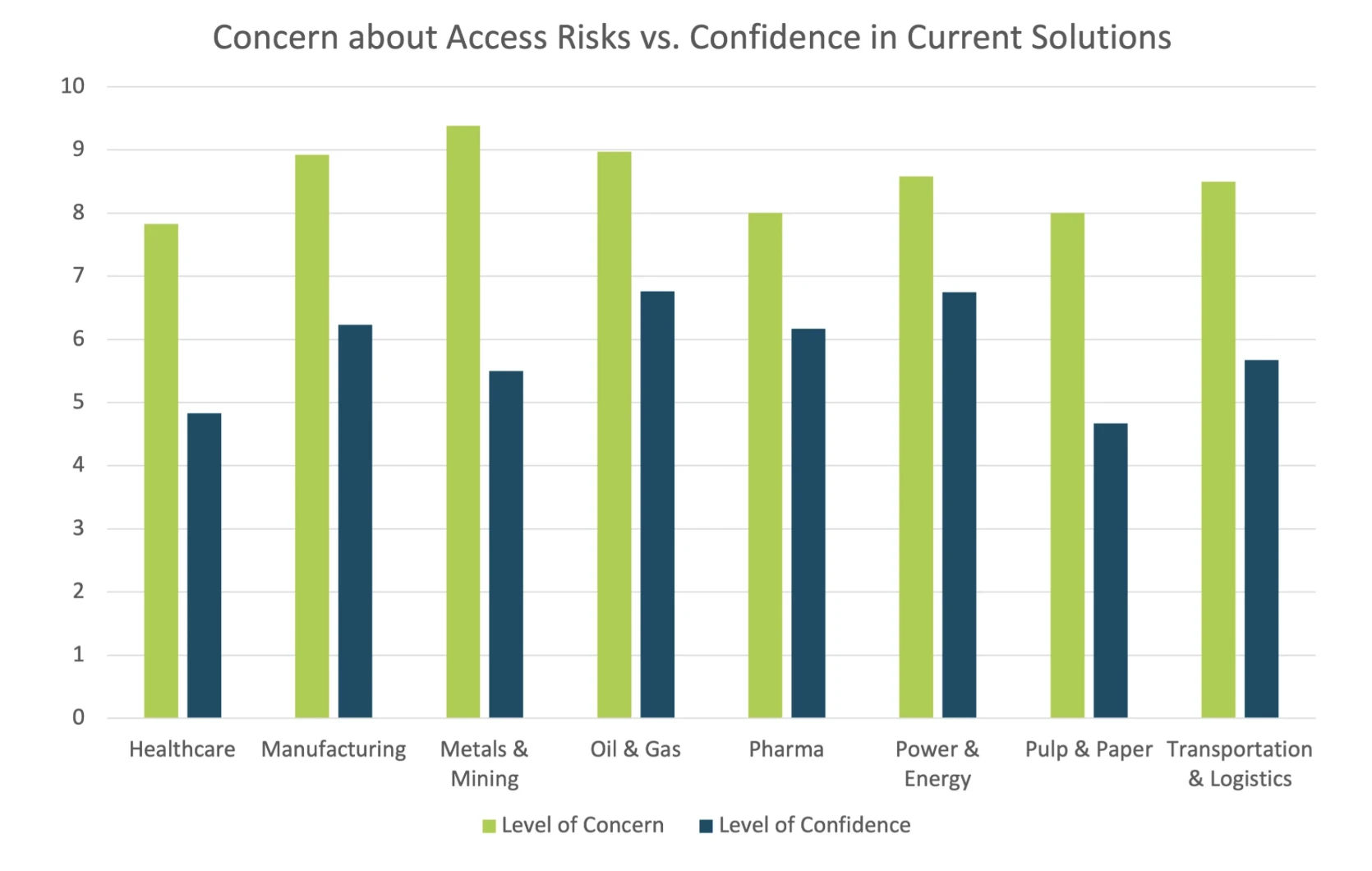
In the Make UK report, the cost of cybersecurity products and the added time and/or cost commitment of maintaining security systems are noted as major obstacles to manufacturing businesses becoming more secure. And somewhat paradoxically, over a third of respondents (37%) report it was in fact the threat of additional cyber risk that stopped them from investing in technological advances supporting interconnectivity. This is indeed the double-edged sword that industrial enterprises across sectors are currently confronting; when implemented well, digitalization and IT/OT interconnectivity can both improve security and productivity; however, without the proper implementation and investments, these advancements can have the opposite effect.
What Are Manufacturers’ Biggest OT Security Concerns?
Knowing what you are up against is the first crucial step toward mounting an effective defense. The Make UK report calls out three core areas that respondents see as their top operational technology security concerns:
Maintaining legacy IT (45%)
Limited cybersecurity skills (38%)
Providing secure access to third parties (33%)
Let's drill a little further into each of these answers.
Most organizations today depend on at least one legacy system, and manufacturers and other industrial enterprises likely rely on several. These systems cannot be easily patched or updated and, as they gain connectivity, they become increasingly vulnerable to cyberattacks. Legacy systems typically do not even support strong identity authentication, making it impossible to enforce basic security measures like multi-factor authentication (MFA). Given these realities, it is easy to understand why survey respondents expressed concern about the security risks of maintaining legacy IT.
The cybersecurity skills gap is another very real concern. Many companies, and especially smaller ones, simply do not have the in-house know-how or resources to either identify which security solutions are needed or to effectively operate them. In fact, over a quarter of respondents (27%) also chose “understanding IT security versus OT security” as a top concern.
The problem of limited cybersecurity skills is closely related to the issue of providing secure access to third parties. When in-house expertise is lacking, organizations logically turn to third-party vendors and specialists. This makes complete sense from the business perspective, but third-party users can create substantial risk if their access to critical systems is not secured and controlled. Companies that rely heavily on third-party vendors can significantly reduce risk by adopting a secure hybrid access platform like Cyolo.
The Material Impact of a Cyberattack
In another interesting section of the Make UK report, respondents were asked about the most impactful consequences of a cyberattack on their business. Over 65% reported disruption to operations as the most damaging post-attack outcome. This response is not surprising given that availability of systems is the number one priority for industrial enterprises. Even a short disruption can result in physical harm as well as very substantial financial costs. According to Comparitech research, “From 2018 to July 2023, 478 manufacturing companies [across the globe] suffered a confirmed ransomware attack, losing an estimated $46.2 billion in downtime alone.”
Manufacturers participating in the Make UK survey also noted damage to reputation with customers/suppliers (43%), unauthorized access (30%), and intellectual property theft (20%) as major business ramification following a cyberattack.
Conclusions on the ‘Cyber Security in UK Manufacturing’ Report
The Make UK study provides a valuable glimpse into the nature of cyberthreats facing UK manufacturers and their global counterparts. Manufacturers today, wherever they are located, are in a unique and complicated position. In many instances, the organizational attack surface has expanded massively due to IT/OT convergence. Previously isolated OT systems are now connected to IT networks and sometimes even the internet, exposing their sensors, instruments, and devices to new and dangerous vulnerabilities. The situation is further complicated by the prevalence of difficult-to-secure legacy technologies and the need to connect third-party vendors to critical systems.
Yet even in this complex new cyberthreat reality, too many manufacturers appear to still believe that using technologies such as antivirus and firewalls are sufficient. According to the report, "approximately 12% of the industry implements this first line of defense… but has not, at least yet, gone further with implementing more robust cyber-secure technologies." The robust technologies referred to include secure settings for devices and software as well as controlled access to electronic data and systems.
Despite the clear challenges facing manufacturers in the UK and beyond, the report ends on this encouraging note:
"OT cybersecurity should not be driven solely by fear. It should seen as a competitive advantage that leads to having secure, reliable and trustworthy products and services that enable greater business opportunity."
At Cyolo, we agree fully with this conclusion. Our secure access platform was purpose-built for deployment in OT environments and can help manufacturers overcome the concerns expressed in the Make UK report. Learn more or schedule a demo today.

Jennifer Tullman-Botzer
Author
Jennifer Tullman-Botzer has over a decade of experience in cybersecurity marketing and is as tired as you are of hackers-in-hoodies stock images. She joined Cyolo in 2021 and currently serves as director of content marketing.

Subscribe to Our Newsletter







