Table of Contents
- Industrial Organizations Say Goodbye to Isolation and Hello to Wide-Ranging Connectivity
- 77: The Average Number of Vendors with OT Envrionment Access per Organization
- 44: The Percentage of Organizations That Are Concerned or Highly Concerned about Third-Party Risk
- Now: The Perfect Time to Secure Third-Party Access
Industrial Organizations Say Goodbye to Isolation and Hello to Wide-Ranging Connectivity
Isolation was long the standard for protecting operational technology (OT) systems from not just cyberthreats but all external influence. However, in recent years the pendulum has swung in the opposite direction, and connectivity is now encouraged or even expected. As organizations adapt to this new reality, they are faced with a number of significant challenges, many of which are addressed in a new research report produced by the Ponemon Institute and sponsored by Cyolo. To create the report, the Ponemon Insitute surveyed 1,056 security professionals in various industries across the US and EMEA.
The report’s findings reveal major gaps in industrial organizations’ current efforts to manage OT systems access and risk, ranging from a lack of awareness about existing security tools to a tendency to begin IT/OT convergence projects without implementing needed security and access management protocols. In this blog, we’ll focus on one specific area of the report: how organizations are coping with the need to enable third-party access to the OT environment in the face of substantial risks.
We have written extensively on this blog about why many industrial enterprises depend on third-party labor and services, but some of the most common reasons include:
The plant and factory managers who often oversee OT environments are rarely security experts and therefore rely on third-party specialists to provide their expertise.
Many original equipment manufacturers (OEMs) require their own technicians to have exclusive rights to perform maintenance on their products.
OT systems are meant to be set up and then largely left alone, with minimal human intervention. As a result, it doesn’t always make sense to hire dedicated OT security personnel in-house.
So, allowing third-party vendors and contractors to access the OT environment is in many cases a necessity. But given the risks they present, third parties should be treated as privileged users whose access permissions are secured to an even greater degree than the average user. According to the Ponemon research, this is not presently happening at most organizations.
77: The Average Number of Vendors with OT Envrionment Access per Organization
73% of respondents to the Ponemon survey reported that their organization permits vendors and other third parties to access the OT environment. Breaking this number down, 43% allow both on-site and remote access for third parties, while 30% permit on-site access only.
Perhaps most notably, the average organization allows 77 third-party vendors to access the OT environment – and 25% of organizations give such access to more than 100 vendors.
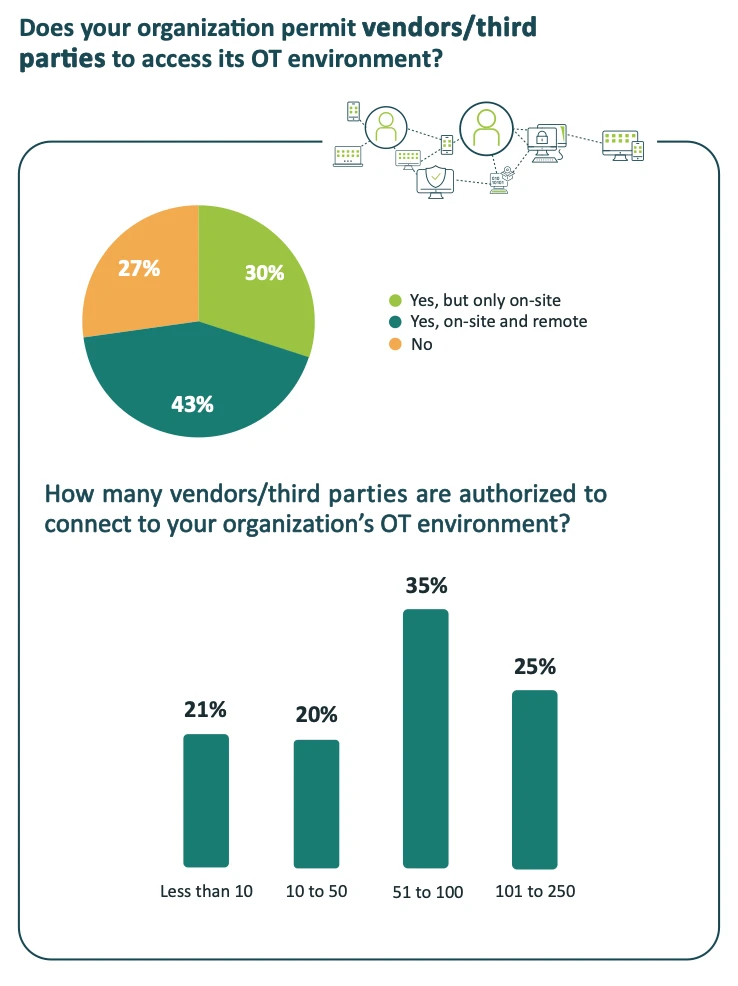
Again, working with third parties and giving them access to internal systems are not inherently bad practices. But it is potentially very dangerous for organizations to allow third parties to move freely through their networks without any access or oversight controls, as this creates a serious risk of malicious or accidental data exposure, system downtime, and other operational disruptions. And the risk only increases with each additional vendor who’s granted access to the OT environment. Organizations that authorize 77 (or more) different third parties to access mission-critical systems are in effect taking on the attack surface of each one of the vendors, plus the attack surfaces of the vendor’s vendors. Should any user or device along the chain be compromised, it could lead to catastrophic consequences for all parties.
Unfortunately, the Ponemon research indicates that many organizations may not be fully aware of the risk they are taking when they authorize dozens of third-parties to connect to their critical OT systems.
44: The Percentage of Organizations That Are Concerned or Highly Concerned about Third-Party Risk
A 2024 SecurityScorecard study found not just that nearly 29% of all breaches in 2023 were attributable to a third-party attack vector but also that a whopping 98% of companies are associated with a third party that has experienced a breach. Yet, even as they open their OT environments to third-party vendors and contractors, fewer than half of respondents (only 44%) to the Ponemon survey said their organizations are concerned or highly concerned about the risks of third-party access. In the EMEA region, only 39% are concerned or highly concerned.
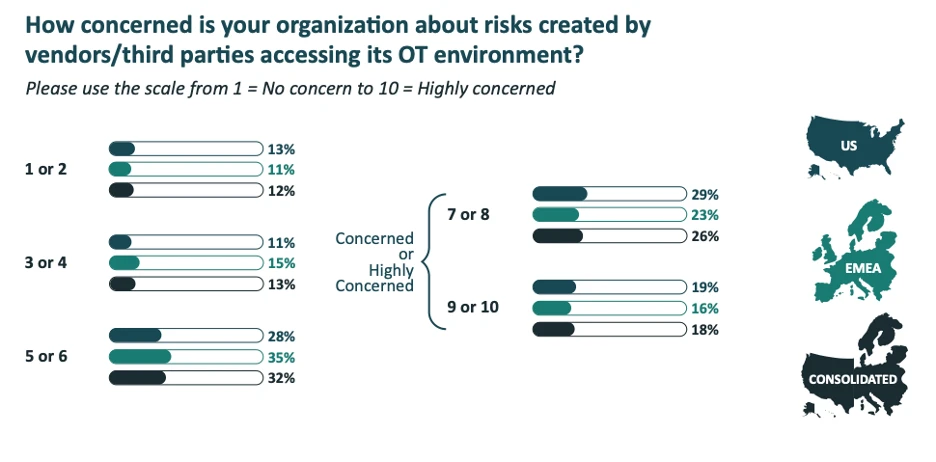
A variety of factors likely contribute to this disconcerting finding – from other competing priorities to a lack of awareness about third-party risk to the simple (but probably unfounded) assumption that their vendors have a strong security posture.
What is clear though from the Ponemon research is that many if not most industrial organizations have not yet implemented the security and access management solutions necessary to combat the risks of third-party access. Only 55% believe their organization is effectively or very effectively mitigating risks and security threats to the OT environment, and more than a third identify the following as challenges specifically to securing third-party access: lack of expertise (46%), lack of budget (42%), budget is committed to other projects (38%), and lack of available solutions (38%).
Now: The Perfect Time to Secure Third-Party Access
Organizations today cannot afford to implicitly their trust third-party vendors to employ best practices when connecting to the OT environment, nor can they blindly assume that vendors’ security posture meets a high standard. To protect critical infrastructure and keep operations running smoothly, industrial organizations must implement identity-based access for third-party users and devices, and gain real-time visibility into the network activity of everyone accessing their systems.
The good news is despite many Ponemon survey respondents reporting a lack of solutions, there are in fact tools available today that can drastically lower the risks of third-party access. The Cyolo PRO (Privileged Remote Operations) secure access solution enables organizations to safely connect third parties, including OEMs, to OT environments for enhanced productivity.
Learn more about Cyolo PRO and read the complete Ponemon Institute research report for more insights into how organizations are coping with threats to the connected OT environments.
New from Ponemon Institute:
Managing Access & Risk in the Increasingly Connected OT Environment

Jennifer Tullman-Botzer
Author
Jennifer Tullman-Botzer has over a decade of experience in cybersecurity marketing and is as tired as you are of hackers-in-hoodies stock images. She joined Cyolo in 2021 and currently serves as director of content marketing.

Subscribe to Our Newsletter







