As organizations continue to adopt more and more born-in-cloud technologies, their technology stacks are growing to include more and more components: containers, servers, databases, end-user devices, S3 buckets, and more. The convoluted nature of this architecture makes it difficult to govern and control them. Components that are connected to the public internet are especially vulnerable, since they can be more easily accessed and exploited by attackers.
Such connected components could be exploited by cyberattackers in various main ways, for example:
When a default password hasn’t been changed, as in the case of SolarWinds, attackers can enter the password and access systems as though they are an authorized user.
When a public component has a vulnerability that hasn’t been patched, as in the case of Log4Shell, attackers can run malware that bypasses the vulnerability and access the network.
When a public component runs an open-source component, its code may be analyzed for previously unknown (zero-day) vulnerabilities.
To identify these public vulnerabilities, attackers can use various Open Source Intelligence Techniques (OSINT), which collects data that is publicly available. In this blog we will examine three reliable OSINT methods attackers use to identify public vulnerabilities and exposed components.
Three Common OSINT Methods
OSINT Method #1: Google Hacking
Google Hacking, also known as Google Dorking, is a hacking method that makes use of the Google search engine. Through advanced search, hackers look for vulnerabilities in website code and configurations. Such vulnerabilities can be found in various public assets, like log files, public FTP servers, configurations, private keys, SQL documents, cached website versions, and more. These could all contain critical information that can be exploited.
To search for these assets, the only thing hackers need to do is use Google to search through a website or domain. Google enables easy searching in websites, titles, URLs and other components by typing in [insite:<sitename>], [intitle:<titlename>], [inurl:<urlname>], etc. Then, attackers can continue and search for specific file types, versions, keys, publicly connected devices, etc., which could indicate an exploitable vulnerability.
Google Hacking is a nefarious method for attackers because of Google’s powerful crawling capabilities, along with the immediate availability and accessibility of the service. In other words, attackers can easily search for large volumes of exploitable information at minimal cost and effort.
OSINT Method #2: Monitoring Certificate Transparency Logs
Certificate Transparency is a security standard that monitors and audits website digital SSL certificates. Verified certificates, such as those that were issued by certified Certificate Authorities, are aggregated and recorded in a public database. With Certificate Transparency databases, organizations can gain visibility into their certificates and identify any misused certificates or vulnerabilities that could expose it to a breach. CRT.sh, for example, is one such website that enables extracting Certificate Transparency logs and reviewing their information.
However, not only domain owners can access websites like CRT.sh. The website is accessible to anyone, and hackers can use it to search for certificate logs per domain or organization name.
Searching the site will reveal a list of certificates, which might include information about vulnerable exploitations that can be used for phishing, stealing credentials or identifying unintentionally exposed assets. To exploit these certificates, attackers will try to automatically access and breach whichever domains those certificates were issued for.
In this case, the same information used by organizations to identify vulnerabilities can also be used by attackers, especially if they catch it earlier than the organizations do.
OSINT Method #3: Public Scanners
Public scanners and search engines like Shodan.io scan the public network and identify publicly-connected devices like cameras, medical devices, and more. Any publicly-connected device is crawled and aggregated in a publicly accessible database. Anyone can use these scanners, including attackers.
Here’s what a Shodan report looks like:
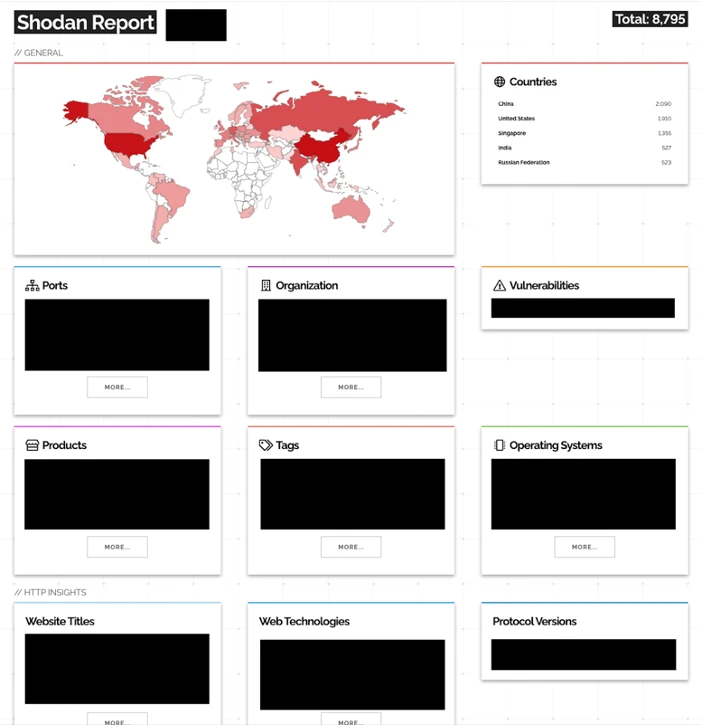
As you can see, the information available in the database is technologically advanced and includes geographies, ports, organizations, operating systems, and more. After searching, attackers can look into the data and gather information that will help them attack.
For example, they can try to identify technologies with CVEs and then run malware or perform brute force attack campaigns on them. If the organization hasn’t patched the vulnerability yet, the threat actor could be able to access the network.
Defending Against OSINT-based Attacks
When it comes to public vulnerabilities and OSINT-based attacks, the main challenge security and IT teams have to deal with is trying to airgap all risks at any given time. It takes only one exploitable vulnerability to give attackers what they need to access the network, progress laterally, and breach valuable data. This is a zero sum game – and a difficult and stressful task.
New vulnerabilities are reported regularly, with over 22,000 reported in 2021. Each new report creates an attack vector that must be secured, so security teams remain vigilant. It is not possible to avoid the impact of vulnerabilities, and patching software, devices, or applications is not a reliable way to mitigate this onslaught of issues. The common method is network isolation, or segmentation, to enforce access control, but this method is also unreliable.
Despite the challenges they create, publicly exposed components are essential for business operations and therefore cannot be blocked. Today’s business needs require global connectivity to the public internet: for accessing websites, SaaS applications, remote work, and for successful third-party cooperation.
With new vulnerabilities and easy tools to locate them, the reality is that companies are more exposed than ever before. To reduce the risk of a data breach, security teams should employ an advanced secure remote access solution that adheres to the principles of zero trust and provides full control of insider access.

Eran Shmuely
Author
Eran Shmuely is the Chief Architect and Co-Founder of Cyolo. Prior to Cyolo, Eran was the Senior Security Engineer at Salesforce and the Open-Source Security Research Leader at GE Digital.

Subscribe to Our Newsletter







